Azure Virtual Desktop technical (ARM-based model) deployment walkthrough. It covers all you need to know and beyond!
Are you interested in the new Windows 365 cloud PC service? Please read Get started with Windows 365 – Microsoft Tech Community to learn more!
The new Azure Virtual Desktop (AVD) Azure Resource Manager (ARM) based model is now Generally Available for everyone – and the interest is enormous. It addresses a lot of customer feedback, such as extra management (GUI) capabilities, AAD group support, metadata location changes and more… AVD can be a good fit for different kind of scenario’s to enable remote working.
In this article, I’d like to cover the deep(er) technical points, while some are just not part of the public message but still way too important not to share. It’ll hopefully help you as consultant or architect to bring the technical (and functional) message around Azure Virtual Desktop – ARM-based to your customers 😊! Continue reading…
Table of Contents
Click on the title to jump to that spot in this article:
- New! Windows in the Cloud – video show with Christiaan Brinkhoff
- Windows in the Cloud – get started with Windows 365 cloud PC
- Azure Virtual Desktop at Enterprise scale – documentation
- Azure Virtual Desktop Deployment Recommendations and Best Practices webinar
- New Azure Portal – Dashboard
- Differences between AVD non-ARM and ARM
- New user management options
- Custom RDP Settings via Azure Portal
- Delegated Access via Azure RBAC – Access control (IAM)
- New PowerShell Modules
- Manage Azure Virtual Desktop via Microsoft Endpoint Manager (MEM)
- MSIX app attach (via the Azure Portal) – The future of app delivery
- Azure Virtual Desktop and Azure Log Analytics
- Screen Capture Protection
- Azure Automation – auto-scaling tool
- Start VM on Connect
- Once more – What is Azure Virtual Desktop?
- The architecture behind it all
- AVD User connection Traffic Flow
- Azure Virtual Desktop service network access requirements
- Measure your latency – tools
- RDP Shortpath
- Manage Windows 10 multi-session via Endpoint Manager (MECM)
- What about GPUs?
- Azure Virtual Desktop – ARM based portal enrolment process
- Pre-requisites for Azure Virtual Desktop
- Create an custom Windows 10 multi-session image
- Install OneDrive Per-Machine
- OneDrive Known Folder Move – modernize your profile
- Install Teams with AV Redirection media optimizations
- Add language packs
- Add FSLogix Profile Container as profile delivery solution
- Additional image optimizations
- Sysprep the image
- Capture the custom – Azure Managed – image
- Optimize your images with the Virtual Desktop Optimization tool
- Create an Azure Shared Image Gallery (SIG)
- Perform the Microsoft.DesktopVirtualization resource provider registration
- Create a host pool
- VM details
- Administrator account
- Create the Workspace
- Select your image type
- Network and Security
- Start enrolment
- Create and Assign Remote Applications (to AAD Groups!)
- Expand your existing host pool with new session hosts
- Update the host pool images – create a new image version
- Change the name of your Workspace
- Change the name of your Virtual Desktops
- Install the Azure Virtual Desktop Client
- Do you prefer to enter your organization’s email?
- Deploy the Remote Desktop Client via Microsoft Endpoint Manager – Intune
- Use the HTML5 Web portal
- Want to see everything above in action?
What is Windows 365?
Users want technology that is familiar, easy to use and always available so they can work and create fluidly across devices. cloud PC makes this possible by combining the power and security of the cloud with the familiarity of the PC. Only Microsoft can bring together the PC and the cloud with a consistent and integrated Windows experience. Introducing Windows 365. Windows 365 is the world’s first cloud PC. With a cloud PC, Windows evolves from a device-based OS to hybrid personalized computing.
A cloud PC is your personalized desktop, apps, settings, and content streamed securely from the cloud to your devices. It enables you to decrease costs while lowering the complexity of your environment as you deploy and manage virtual endpoints in Microsoft Endpoint Manager. No additional virtual desktop infrastructure (VDI) expertise or resources are needed.
In addition, Windows 365 enables you to:
- Procure, provision, and deploy in minutes, with optional automated OS updates.
- Offers user anywhere access to their personalized Windows desktop experience.
- Tailor compute and configurations for an elastic workforce.
- Pick up where you left off on the device of your choice.
- Optimize experiences on Windows endpoints.
- Scale confidently with per-user pricing.
Removes the complexity of traditional VDI deployments
With Windows 365, all the building blocks are automated for you and we make sure that the service scales with you in the most optimized way possible to use Microsoft 365 apps. It is Microsoft’s best expression of Windows and Microsoft 365 and is always secure and up to date.
The cloud PC can be accessed anywhere from any device and can scale with a user’s changing compute needs, meaning that the user could receive the self-service privileges to release an IT admin from assigning a license that provide more compute resources. The same applies for storage upgrades and cloud PC reboots, more about this later.
Read more about Windows 365 here Get started with Windows 365 – Microsoft Tech Community
New! Windows in the Cloud – video show with Christiaan Brinkhoff
This live Microsoft Teams webcast series highlights new features, best practices from both Microsoft Engineering and the community, and Windows 365 success stories. We hope you’ll join us right here as we explore technology-focused topics alongside members of the community, Microsoft Engineering, customers, and users.
In episode 1, Jen Gentleman from the Windows Engineering team showcases new features to help you be more productive in the cloud as part of Windows 365. The session is fully demo-driven. It gives you an inside view of all the new features and explains how they came into Windows 11, Microsoft’s newest operating system.
Click here for more information – or watch all the recordings and to see all the new upcoming episodes.
Azure Virtual Desktop at Enterprise scale – documentation
As part of a great Microsft internal field initiative that I led we created two very important articles on how to use Azure Virtual Desktop as well as FSLogix at Enterprise scale. The articles include tons of best practices and tips and tricks that get you up to speed proactively while designing a large virtual desktop infrastructure on Microsoft Azure.
- Azure Virtual Desktop for the Enterprise: aka.ms/wvdbestpractices
- FSLogix for the Enterprise: aka.ms/fslogixbestpractices
Azure Virtual Desktop Deployment Recommendations and Best Practices webinar
Recently, I’ve presented a webinar on the above content. This information could be very valuable for everyone that is using this blog article to kick the tires on Azure Virtual Desktop.
Get guidance on:
- Virtual machine sizing requirements for single and multi-session to help maximize usage and performance.
- Preparing your network for Microsoft Teams to support remote worker collaboration.
- Managed storage options to optimize FSLogix profile containers for your user and regional requirements.
- Optimizing your host pool and image gallery setup for the best user experience.
Azure Portal – Dashboard
The new landing page for Azure Virtual Desktop in the Azure portal looks like this. It’s very slick and steps are dramatically simplified. Previous steps such as consent and PowerShell creation of the tenant are all gone! Learn more about it later on in this article.
Differences between AVD non-ARM and ARM
The new Management portal integration is completely built on ARM, which means that permissions can be managed via role-based access control (RBAC). All the deployment objects of AVD e.g. host pools, workspaces, etc are objects within your Azure subscription. This makes it easier to manage and automate your environment.
See below the most important differences and changes of classic AVD (non-ARM) and AVD ARM-based via the Azure Portal.
User session management
With the new ARM-based – spring update release of Azure Virtual Desktop being available. We also have the option to do more user session troubleshooting directly from the Azure Portal. The users menu option gives us the option to search for users, see their active sessions, application assignment, and send them messages during maintenance work.
This allows helpdesk employees to do some first line of support for Azure Virtual Desktop from the Azure Portal.
Note: If you are interested in learning about the different options to remote control/shadow user sessions, please use one of my other blogs as here to learn more.
Custom RDP settings
Previously in the non-ARM version of Azure Virtual Desktop, you had to activate RDP settings via PowerShell. In the new ARM-based model it’s possible to turn for example clipboard or disk drive redirection to align with your company security baselines and perform this step directly from the Azure portal menu.
Delegated Access via Azure RBAC – Access control (IAM)
Since Azure Virtual Desktop made the shift to Azure Resource Manager (ARM), a lot of extra options to delegate access to your AVD components are possible. This works via RBAC/IAM roles. The role assignment process has three components: security principal, role definition, and scope. The new roles are now directly available from the Azure Portal. Learn more about delegation via RBAC roles and Azure Virtual Desktop here.
PowerShell Modules
As part of this release, AVD now also integrates into the AZ PowerShell module. Commands are now starting with e.g. Get-AzWvdDesktop instead of Get-RDSDesktop. This leaves up to still create all the Azure Virtual Desktop components completely automated via PoSH. ARM templates for doing the Workspace (tenant), host pools and application group deployments automated are coming soon. More information can be found here.
Note: The new ARM templates for Azure Virtual Desktop ARM-based to automate your deployment are now available for download here.
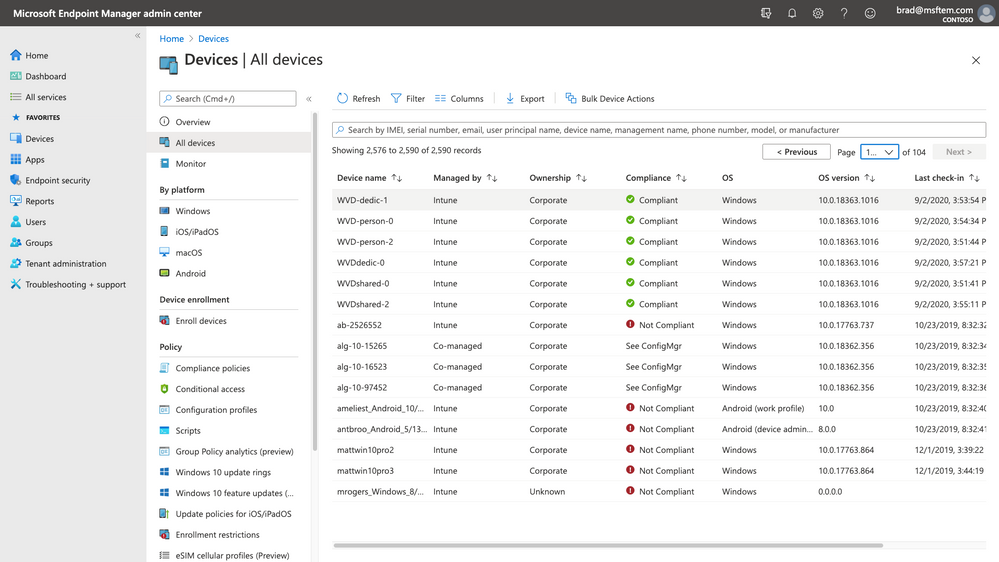
Manage Azure Virtual Desktop via Microsoft Endpoint Manager (MEM)
Microsoft Endpoint Manager allows you to manage policies and distribute applications across devices. You can now enroll Azure Virtual Desktop virtual machines that are hybrid Azure Active Directory domain-joined (joined to your on-premises Active Directory and registered with your Azure Active Directory) with Microsoft Intune and manage them in the Microsoft Endpoint Manager admin center the same way as physical devices. This simplifies management, provides a centralized view across both physical devices and virtual desktops and creates new areas of collaboration. The Microsoft Endpoint Manager integration is generally available for Windows 10 Enterprise desktops – you can learn more in the public FAQ.
Expect more and more consolidation between physical and virtual desktops in the near future. One simplified management console to maintain both physical and virtual desktops!
See below Windows 10 Enterprise virtual and physical desktops coming together in Microsoft Endpoint Manager.
The future of app delivery – MSIX via the Azure Portal now available!
4.13.2021 update – MSIX app attach is now available in GA – ready for production workloads. Read more about the announcement here.
Previously, you had to use PowerShell scripts to enable MSIX app attach. We will be integrating the app attach capability in the Azure portal and Azure Resource Manager. This will eliminate the need for custom scripts and makes it possible to publish your packaged applications to application groups with a few clicks.
MSIX (without app attaches) is a Windows app package format that provides a modern packaging experience to all Win32, UWP, and Windows apps. It’s a new way of doing application virtualization compared to technologies such as App-V.
Adding the app to attach technology makes MSIX more compliant for virtualized desktop environments such as Azure Virtual Desktop. The main challenge within DaaS/VDI around application delivery is around the images and how the apps come into the image. Separating the applications from the image to update and assign applications without doing an image update sounds like the solutions, right? Well, that’s exactly what MSIX app attach can accomplish…
See below the most important benefits:
- Less re-imaging
- Same package format across your entire organization
- No repackaging needed, most likely ISVs will provide packages to customers
- Applications are indistinguishable from app in the OS image
How does the process work?
- AVD Administrator configures and assigns MSIX packages via the new Azure Portal integration
- First, the user authenticates and obtains AVD feed
- Broker connection to VM in host pool happens on the AVD service level
- Load FSLogix user-profiles containers
- Read apps assigned to the user
- Registers applications to the session host e.g. Windows 10 Enterprise
Learn in one of my latest new blogs more about the process to enrol and use MSIX app attach in the Azure Portal with Azure Virtual Desktop, or watch this episode with demos here – at episode 5 of Desktops in the Cloud.
Azure Virtual Desktop and Azure Log Analytics
The main purpose of leveraging Public Cloud is not saving money. It’s around leveraging platform services to adopt as much as services to create the digital workspace for your business.
One of those platform services in Azure is Log Analytics, the service to gather metrics in your environment and bring them down to one single pane of glass dashboard. Log Analytics gives you all the information about sessions. This includes e.g. bandwidth and latency for every single user and session on your site. This can be relevant for troubleshooting or just monitoring purposes, and it doesn’t require any additional investments.
There a lot’s of new metrics and integrations possible now within Azure Virtual Desktop directly from the Portal.
This dashboard below includes insights about the following components of your Azure Virtual Desktop deployment:
- Overview
- Session Details
- Session Diagnostics
- User Specific Reporting
- Session Performance
- Host Performance
- Disk Performance
Update 12.10.2020. Azure Monitor for Azure Virtual Desktop is now also in public preview via the Azure Virtual Desktop Portal. Learn more about it Azure Monitor for Azure Virtual Desktop public preview – Microsoft Tech Community.
Screen Capture Protection
With the new Screen Capture Protection feature in public preview, customers can easily block the creation of screenshots of the virtual desktop session. For example, if you want to protect all the data from going out of the consolidated virtual desktop session, this feature is definitely something you’d like to add on top of your Conditional Access and Azure MFA rules to enhance the data protection level of your Desktops in the Cloud – as part of Azure Virtual Desktop. See below an example for it works, the desktop session that is completely black is where the Screen Capture Protection feature has been enabled. The feature also works when your desktop session is shared via Teams screen-sharing. Learn here how to activate the feature on a Windows 10 Enterprise single or multi-session desktop.
Azure automation – auto-scaling tool
For many Azure Virtual Desktop deployments in Azure, the virtual machine costs of the Azure Virtual Desktop session host VM represent the most significant portion of the total deployment cost. To reduce cost, the AVD Depth-first mode automatically fills up the first session host server maximum amount of users before spinning up the next one, and so on. The other option is to use it to shuts down and de-allocates RDSH server VMs during off-peak usage hours and then restart them during peak usage hours. This can be a huge cost saver!
Breadth mode is the standard – default mode, which is based on Reserved Azure instances (IaaS). With Breadth mode, the users will spread across host pool collection.
Read more about this feature, and download the new Azure Automation Runbook script for ARM-based AVD here.
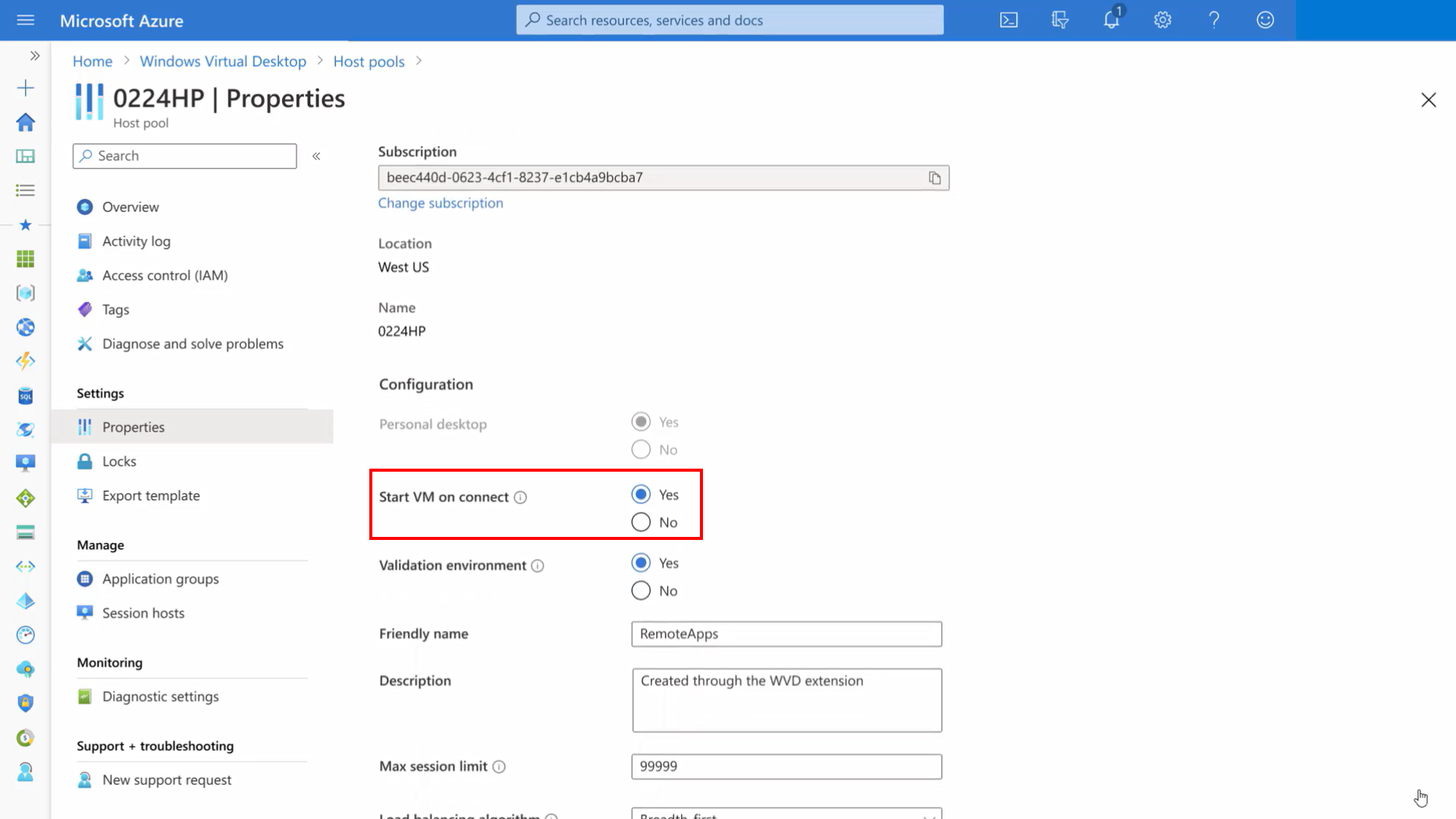
Start VM on Connect
The word is saying it, with the new feature VM start on Connect – you can start the session host while clicking on the icon. This is a huge cost saver as you could shut down your virtual machines while logging off and spin them up the day after.
This feature is only available for personal host pools and is NOW AVAILABLE in public preview. More information: Start virtual machine connect – Azure | Microsoft Docs
Once more – What is Azure Virtual Desktop?
People that follow my blogs know that I explained the services and benefits earlier. However, for the people who didn’t catch that yet, here is a short run-over.
“Azure Virtual Desktop, or AVD in short – is a born in the cloud Managed-platform service offering on top of the Microsoft Azure Cloud. All the infrastructure services, such as brokering, web access, load-balancing, management and monitoring is all setup for you as part of the control plane offering. It also gives you access to the new Windows 10 Enterprise multi-session Operating System – which is completely optimized for the sake of Office 365 ProPlus services, such as Outlook, OneDrive Files on Demand (per-machine), Teams etc.“
The only responsibility in terms of management effort is the golden images on top of Azure Infrastructure-As-a-Service (IaaS). The rest is all managed for you through the Azure service SLAs. Sounds pretty cool, right?
Let’s first start with the things you might not know about it
- Azure Virtual Desktop gives you the only multi-session Windows 10 experience, including compatibility with Microsoft Store and existing Windows line-of-business apps, while delivering cost advantages.
- Allows you to virtualize both Full desktops and RemoteApps.
- You can also use for persistent Windows 10 – single-user virtual desktops.
- AVD will support Windows 7 virtual desktops and is the only way you can safely run Windows 7 after its End of Life on 14 January 2020. Windows 7 desktops on AVD will be the ONLY systems that receive free extended security updates.
- Customers with the following license SKUs are entitled to use AVD with no additional charge apart from Azure compute, storage, and network usage billing:
- To run Windows 10 multi-session, Windows 10
- Microsoft 365 F1, E3, E5, A3, A5, Business
- Windows 10 Enterprise E3, E5
- Windows 10 Education A3, A5
- Windows 10 VDA per user
- To run Windows 7
- Microsoft 365 E3, E5, A3, A5, F1, Business…Windows E3, E5, A3, A5
- To run Windows Server 2012 R2, 2016, 2019
- Remote Desktop Services (RDS) Client Access License (CAL) with active Software Assurance (SA)
- To run Windows 10 multi-session, Windows 10
- Azure Virtual Desktop session host VMs are not exposed to the internet directly. They can run using a private IP address and run isolated from other workloads or even the internet. The reverse connect technology allows the VMs to be accessed
- When a user connects to the AVD service, the use of Azure Active Directory (AAD) as the identity provider allows you to leverage additional security controls like multifactor authentication (MFA) or conditional access;
- Deeply integrated with the security and management of Microsoft 365, such as Intune Modern Management
- From a best practices point of view; Make sure all Azure resources are in the same region
- All the Nvidia vGPU / and the recently announced AMD EPIC CPU/GPU graphical enhanced N-Series virtual machines on Azure are supported with Azure Virtual Desktop.
- Citrix is adding their own Citrix Cloud stack as well to Azure Virtual Desktop, read more about this here.
- VMware Horizon Cloud is now also available as an extension to Azure Virtual Desktop, read more about this here.
The architecture behind it all
The first step that you must do is creating the Azure Managed image, or golden image in VDI terms (or use one pre-build from the gallery). Most often, this will be based on the new Windows 10 Enterprise multi-session Operating System, which is now available from the Azure Marketplace. After enrolling in the server, you can start installing the application on the machine. When you’re done, you must capture the machine as an image to use as a base for your Azure Virtual Desktop deployment.
The Microsoft-managed control-plane is a completely redesigned infrastructure that leverages native Azure platform services to scale automatically. Think about Azure front-door as a global load-balancer for the RDP connection, Azure App Services in Azure for hosting the infrastructure services, and Azure SQL DB for hosting the RDS Brokering databases. Leveraging these services is the main reason why this service is so cost-effective, which is the purpose of the Cloud and what it’s built for!
AVD User connection Traffic Flow
To give you a better understanding of how Azure Virtual Desktop connections work, I’m sharing the traffic flow (the traffic flow requires the following network URL and protocol access). This is also useful for troubleshooting purposes.
Connecting from your virtual machine in Azure to your Host Pool (session hosts in Azure Infrastructure-As-a-Service) works differently with Azure Virtual Desktop. It uses Reverse Connect, which means that no inbound ports need to be opened on the VM to setup the RDP connection. Once the connection flow proceeds, bidirectional communication between your session hosts/host pool will go over port https (443). This port is almost always open from the inside to the outside, so it’s perfect for a remote connection to Azure Virtual Desktop!
Azure Virtual Desktop is a global load-balanced service via Azure front-door. This means that the traffic flow below always goes via the nearest management control-plane/service location – which you can see in the middle bucket below.
The service is globally available with management plane in:
Central US, East US, West US 2, North Europe, West Europe, India, Singapore, Australia, South Africa, France, Germany, Norway, UK, Korea, and South America. Available in GA.
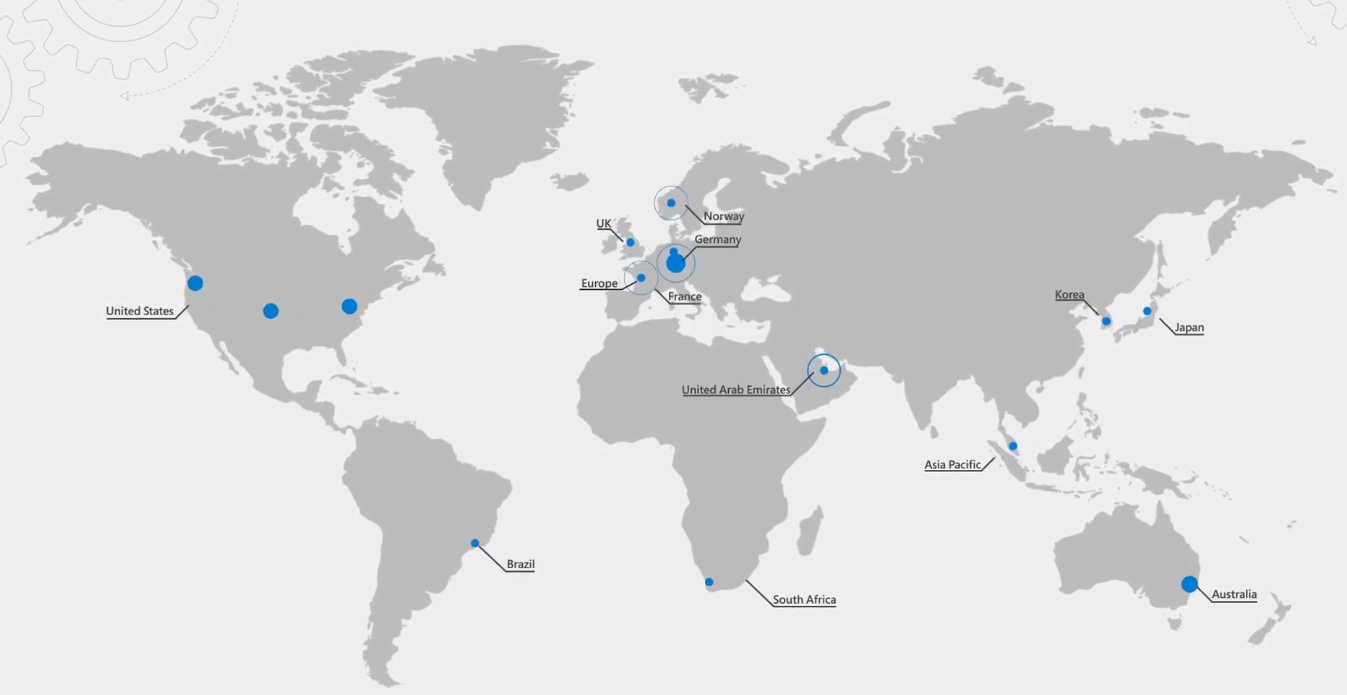 See below in more depth how the traffic flow works.
See below in more depth how the traffic flow works.
- User launches RD client which connects to Azure AD, Azure MFA, user signs in, and Azure AD returns token
- RD client presents token to Web Access, Broker queries DB to determine resources authorized for user
- User selects resource, RD client connects to Gateway
- Broker orchestrates connection from host agent to Gateway
- RDP traffic now flows between RD client and session host VM over connections 3 and 4
Azure Virtual Desktop service network access requirements
To make this traffic flow possible – you need to have at least firewall rules / NSGs / service tags in place for the following network addresses – otherwise, AVD won’t work correctly. When you use an ExpressRoute with force-tunnelling to your local gateway, make sure to configure the routing tables correct, as described for KMS in this article. Within configuring this – your virtual machines won’t be able to communicate to our Azure KMS server. There’s also the option to use Azure Service Tags with all the URLs/Ports pre-configured and auto-updated for you – this could make your life a lot easier. You can find the full list of URLs here too.
Note: If you don’t arrange access at the VNET level to the URLs/Ports below – your deployment most likely will fail!
To connect from the client – endpoint location. The following network access is required to setup the session to the AVD service.
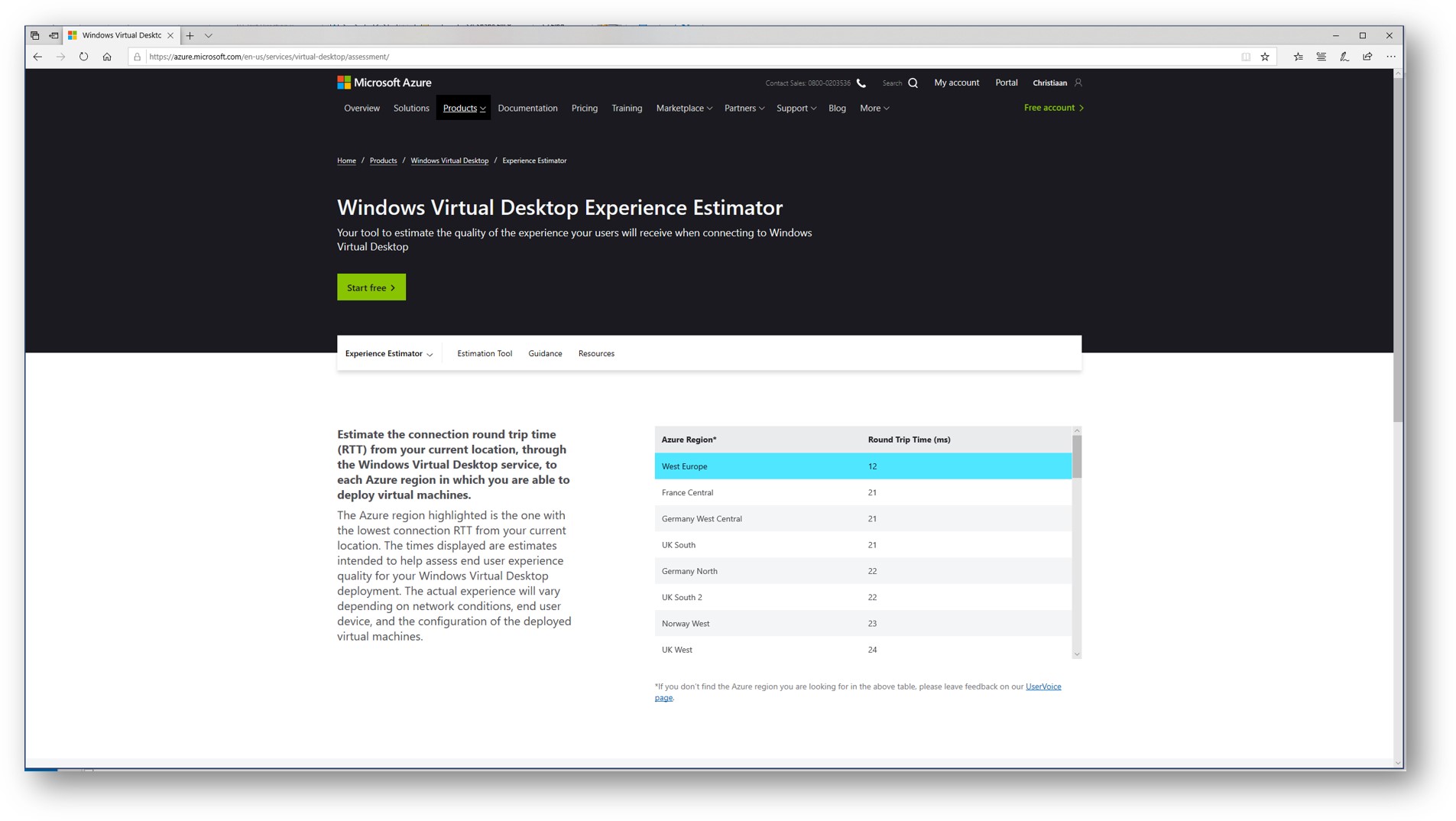
Measure your latency – tools
We can use the online Experience Estimator tool to measure your latency to the nearest control-plane location (as described above) – without deploying a host pool. The tool is web-based and can be found here. The tool measures to the nearest control-plane the latency and as well from the control-plane to the (over the Azure backbone) Azure datacenter region you select to deploy your host pools in.
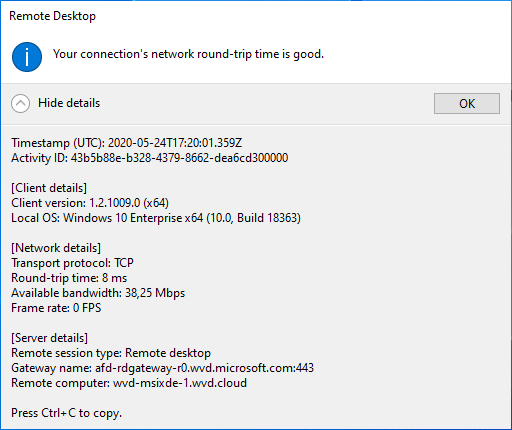
Another option is to use the latest AVD Windows Client and request for the details of the connection. You can request them by clicking on the blue top-middle bar, click on the connection strength icon followed by connection details, and expand the details to see the screen below.
RDP Shortpath
RDP Shortpath is an addition to the RDP protocol to enhance network traffic flow to take a shorter direct route to the session host from the user’s physical endpoint location. It doesn’t replace reverse connect but it builds on top of it to improve the flow and UX. Another huge benefit is that the session (with RDP Shortpath enabled) doesn’t rely on the gateway service anymore – whereof brokering is managed through the Azure Virtual Desktop infrastructure.
In order to use RDP Shortpath, you must have a direct line of sight to the session host – from the physical endpoint via e.g. ExpressRoute, Site 2 Site, or any other VPN service. Enabling the service network addon is relatively simple, you can find the steps to do so over here.
Want to take a deep-dive on RDP Shortpath? Make sure to watch episode #9 about RDP Protocol improvements and RDP Shortpath deep-dive with Denis Gundarev, AVD PM.
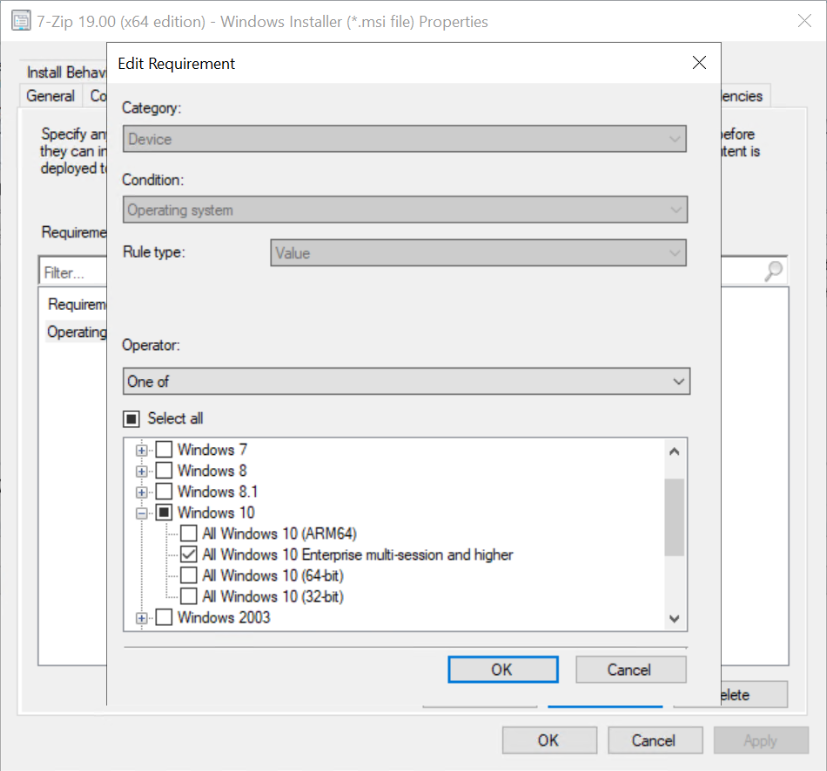
Manage Windows 10 multi-session via Endpoint Manager (MECM)
Since Microsoft Endpoint Manager (MECM) version 2006 – it’s possible to select Windows 10 Enterprise multi-session as a platform in the list of supported OS versions on objects with requirement rules or applicability lists. See below the screenshot of the new option as a requirement for multi-session. Read more about it here.
What about GPUs?
Azure Virtual Desktop – supports graphics acceleration, check out for more information Choose your graphics rendering technology. Azure has other graphics acceleration deployment options and multiple available GPU VM sizes. Learn about these at GPU optimized virtual machines sizes – especially the new Nv4 virtual machines enhanced by a AMD EPIC CPU/GPU are interesting to test due to the fact it supports GPU-P and Premium SSD. More info here.
Talking about GPU and intense workloads? Watch this great episode about pushing the performance boundaries of your Azure Virtual Desktop environment.
Azure Virtual Desktop – ARM-based portal enrolment process
In the next steps, I’ll explain how you enrol Azure Virtual Desktop from scratch with a customer created Windows 10 Enterprise multi-session image among tips and tricks.
Pre-requisites for Azure Virtual Desktop
The following requirements are needed for the use of Azure Virtual Desktop on Azure.
- Azure Subscription
- Azure Active Directory setup
- Azure AD Connect
- Entitled for licensing
- Admin permission to enable resource provider on subscription
- Admin with privilege to create VMs
- (optional) custom image
- Domain controller
- This AD must be in sync with Azure AD so users can be associated between the two
- VMs must domain-join to Active Directory
- Optional: Azure AD Domain Services (in replacement for domain controller)
- Profile Containers network share on Azure Files or Azure NetApp Files (See here our recommended Azure Managed options)
- VNET pre-created with connection to the domain
- Network must route to a Windows Server Active…Directory (AD). See here all the required ports and URLs. – same for the endpoints/client access, find them here.
- Optional: Networking/on-prem connectivity – express route, VPN, etc.
Create a custom Windows 10 multi-session image
Note: You can skip this step and start here if you want to use a Microsoft prepared image with Windows 10 multi-session + Microsoft 365 Apps for Enterprise.
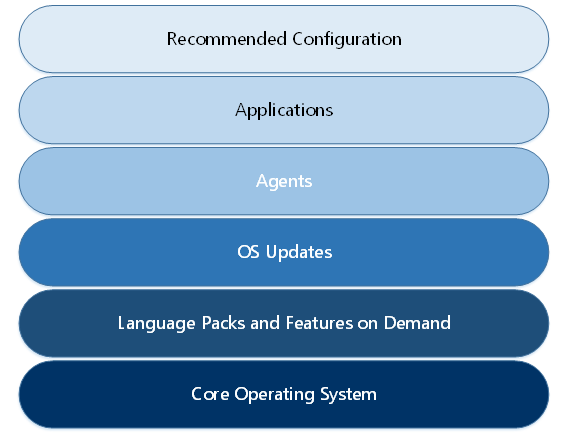
We start with the creation of a custom Azure Managed image (right now based on Windows 10 Enterprise multi-session, however Windows 7 and Server 2012 R2 and higher is supported as well). This image can be used during the new Azure Portal enrolment process to make sure all our new session hosts based on Windows 10 Enterprise multi-session includes all our agents and corporate applications.
During this enrolment we go through different the range of layers, including applications, incorporating language components, and tailoring system settings to adhere to Azure recommendations – to effectively make it customer and end-user ready. Let’s start.
We start with the creation of a custom Azure Managed image(right now based on Windows 10 – multi-session, however Windows 7 and Server 2012 R2 and higher is supported as well). This image can be used during the new Azure Portal enrolment process to make sure all our new session hosts based on Windows 10 Enterprise multi-session include all our agents and corporate applications.
Note: When you want to use a prepared (E.g. Windows 10 multi-session + Office 365 ProPlus) image from the Azure Gallery – please skip these steps and continue here.
Note: The new ARM templates for Azure Virtual Desktop ARM-based are now available for download here.
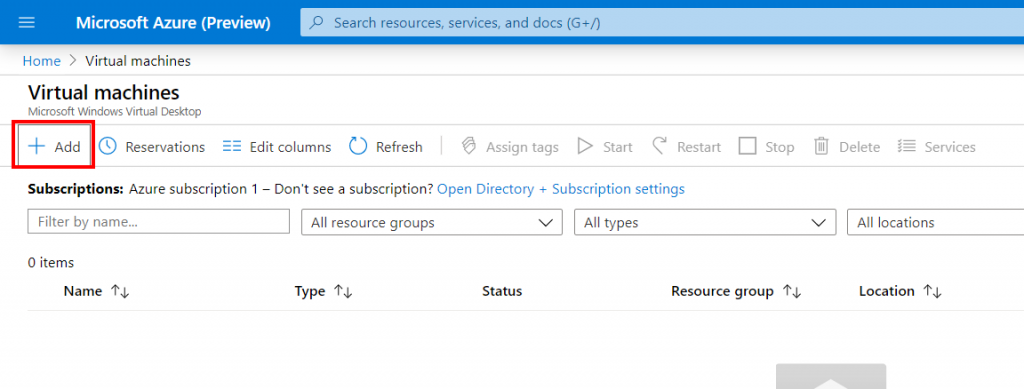
Go to Virtual Machine
Click on + Add
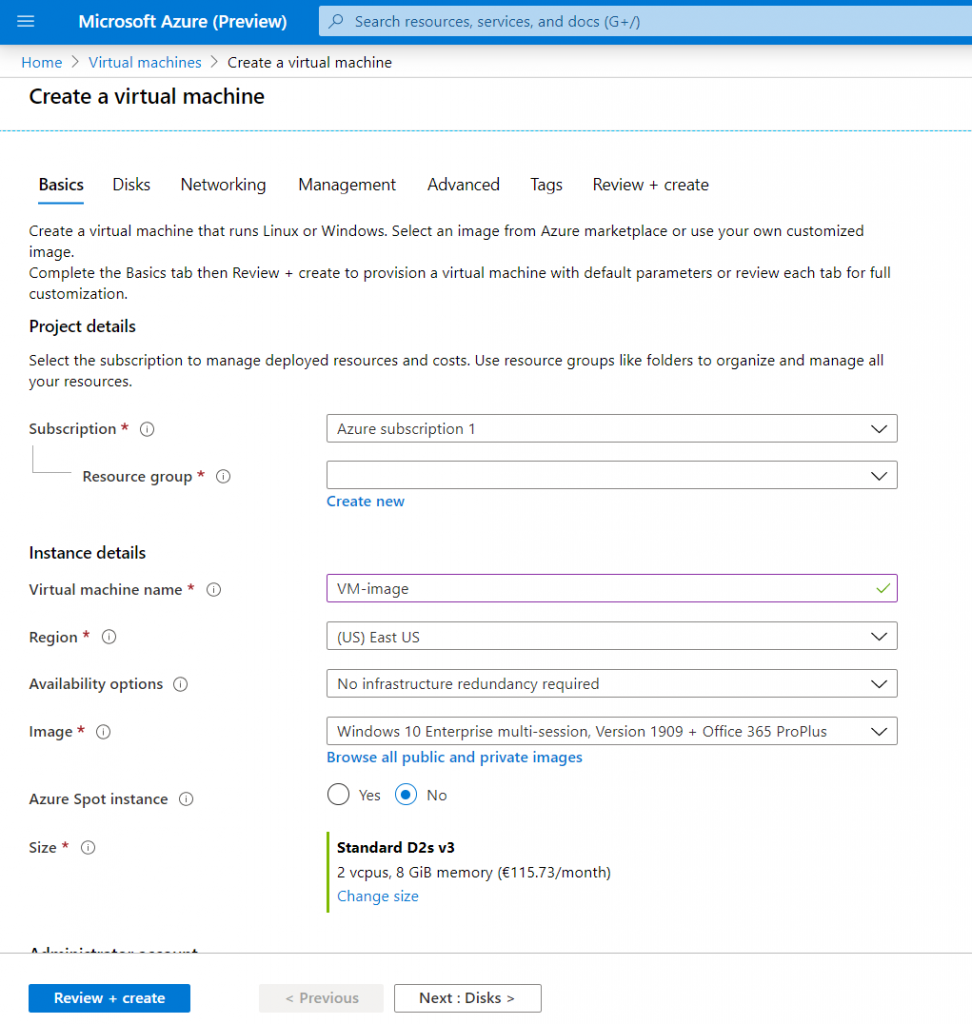
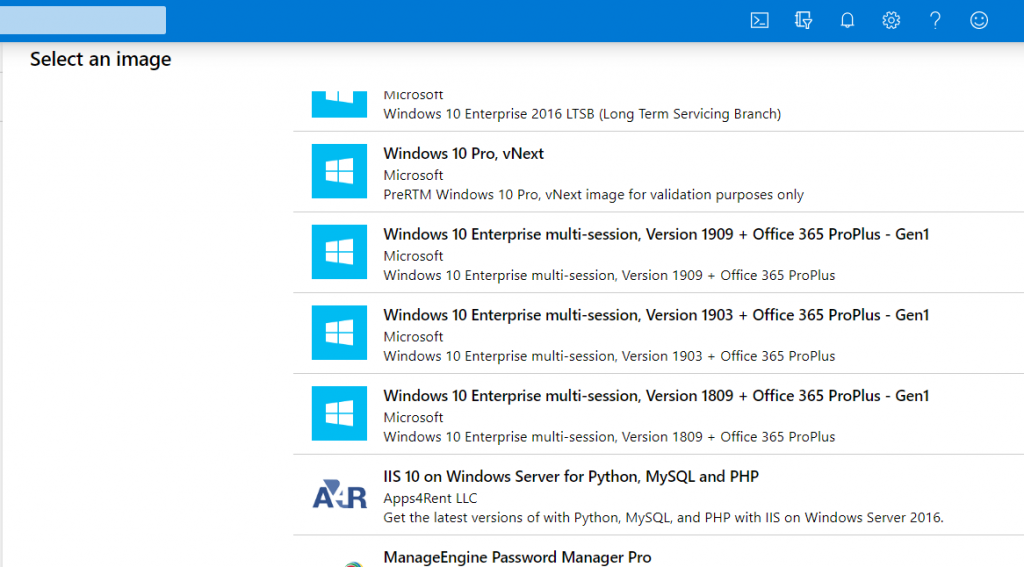
Click on Browse all images
Select Windows 10 Enterprise multi-session + Office 365 ProPlus
Note: Office 365 ProPlus has been renamed to Microsoft 365 Apps for Enterprise.
Once the virtual machine is enrolled and up and running:
Connect – your VM-Image – through Azure Bastion – or RDP to the machine – this can be internally or externally.
Once you are logged on to your master image. Now we can add our agents to the image, such as the FSLogix Apps Agent, plus your own agents and line of business (LOB) – applications.
Install OneDrive Per-Machine
By default, the OneDrive sync client installs per user on Windows, meaning OneDrive.exe needs to be installed for each user account on the PC under the %localappdata% folder. With the new per-machine installation option, you can install OneDrive under the “Program Files (x86)” directory, meaning all profiles on the computer will use the same OneDrive.exe binary.
You can download the new per-machine version of OneDrive below:
https://go.microsoft.com/fwlink/?linkid=2083517
Make sure to re-install the application by using the following command.
OneDriveSetup.exe /allusers
Also, when running this on a multi-session environment, this means that on that same session host, all the different user-profile – OneDrive versions will update simultaneously – which can get messy in terms of network throughput. This is also solved with the per-machine version.
The per-machine version will update itself by a service/account which injects itself during the installation. Therefore, you always need to run the installation as local administrator with UAC privileges.
OneDrive Known Folder Move – modernize your profile
Recently, the OneDrive team added Known Folder Move functionality support to OneDrive, which is very useful to create the same end-user experience for our users on Azure Virtual Desktop as they would have on a Modern Desktop with all profile folders, such as My Documents, Pictures, Favorites, Desktop, etc. redirected to OneDrive. Also, with the use of OneDrive Files On-Demand, you’ll be able to save storage space from your profile folders due to the possibility to work with tiering for your hot and cold data.
While using Known Folder Move on different devices or VDI environments in conjunction with the same OneDrive account. You ensure to always have your Office 365 documents on the same location, everywhere you go! Even on your mobile device, without any notice 😊
Activating Kown Folder Move is relatively easy. You can use the manual approach by opening the OneDrive client from the Start menu and click on Update Folders.
You can also use the automated approach
Enabling this policy sets the following registry keys:
[HKLM\SOFTWARE\Policies\Microsoft\OneDrive]"KFMSilentOptIn"="1111-2222-3333-4444"
(where “1111-2222-3333-4444” is the AzureAD Directory – tenant ID, which you can find in the Azure Portal – under the properties menu of your Azure AD tenant)
In the end, your profile folders will look like this, and are completely in sync with your OneDrive account.
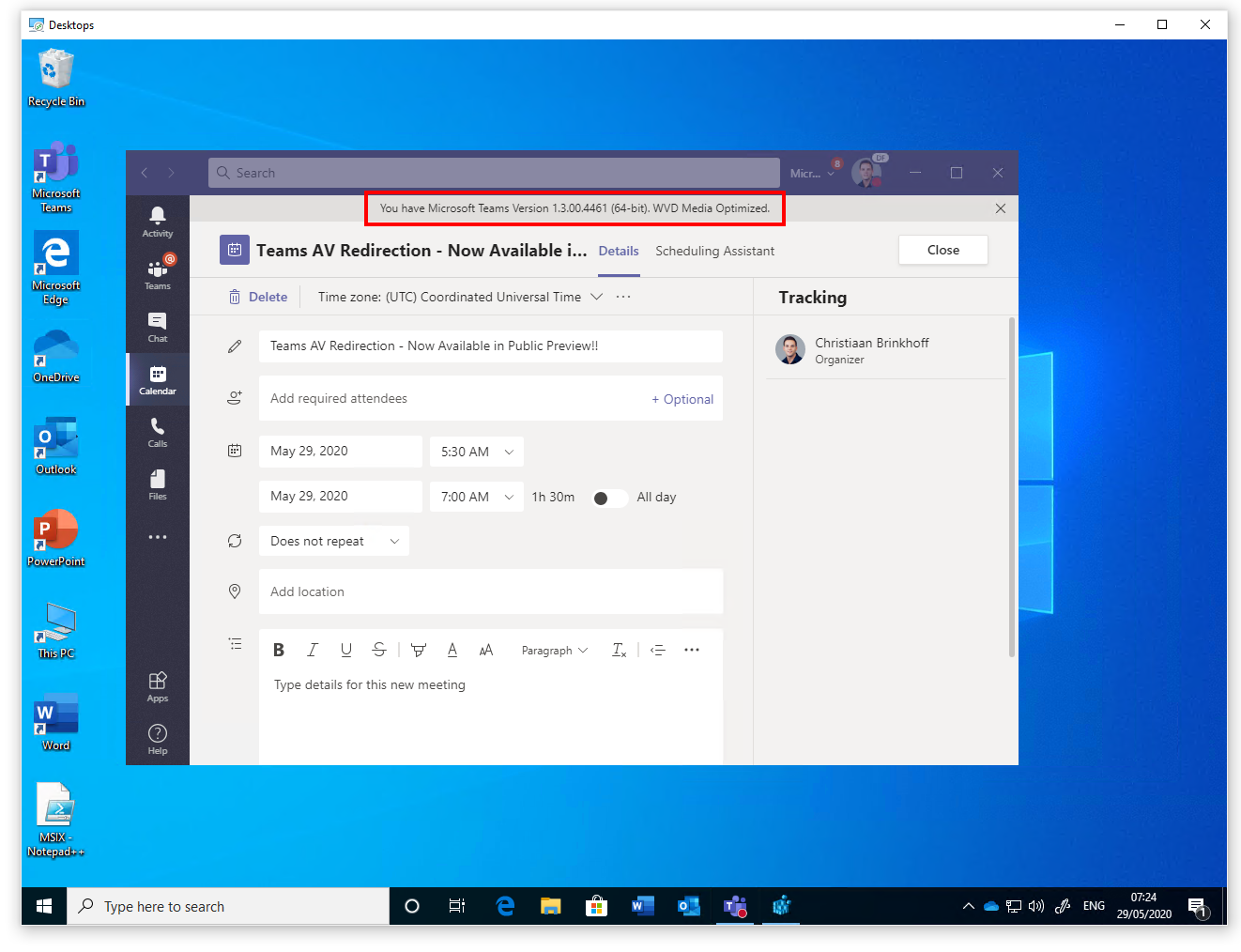
Install Teams with AV Redirection media optimizations
Good news, the long-awaited new AV Redirection with media optimization (WebRTC) client for Microsoft Teams is now available for the Windows Desktop on Windows 10 machines.
Key benefits of this new Teams WebRTC optimizations are:
- High-performance peer-to-peer streaming facilitated by WebRTC – as listed below traffic will flow p2p and rendered via the endpoint
- Devices will be redirected as same hardware device – better hardware redirection support
- On Windows 10 clients, all the benefits of the modern media stack including HW video decoding
- Support for Windows 10 single and multi-session in conjunction with Azure Virtual Desktop.
Note: Media optimizations require Windows Desktop client version 1.2.1026.0 or later – running on Windows 10 as endpoint Operating System. Also, Make sure to optimize your traffic for Teams in general for the use of this client.
First we must create the following registry key in the image
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Teams\
Name: IsWVDEnvironment
Type: REG_DWORD
Value: 1
Download Teams and run the command below to install Teams per-machine
Note: To use the WebRTC AV redirection client, you must use Teams version 1.3.00.4461 or later – the 64-bit version is highly recommended.
msiexec /i c:/install/Teams_windows.msi /l*v < c:/install/Teams.log ALLUSERS=1 ALLUSER=1
If everything ran perfect you will see Teams showing up in the Program Files directory.

Install the WebRTC – Teams WebSocket Optimizations client in your AVD image
Note: When you run into installation issues, please make sure to install the latest Microsoft Visual C++ Redistributable below and try the WebRTC installation again.
- Microsoft Visual C++ Redistributable x64: vc_redist.x64.exe
- Microsoft Visual C++ Redistributable x86: vc_redist.x86.exe
When everything goes as expected. Please start Teams – go to the About settings of your Teams Client inside your session host.
Please go to this docs article if you encounter any issues regarding the public preview.
Add language packs
Make sure to following the steps in this article to add additional languages to the Azure Managed Image.
https://docs.microsoft.com/en-us/azure/virtual-desktop/language-packs
Add FSLogix Profile Container as a profile delivery solution
Note: If you are interested in how you could Azure Files or Azure NetApp Files within AVD. Please consider one of the two articles below in addition to this blog. You can find ALL the differences between the two options here.
In general IOPS between 5 and 15 (depending on workload/amount of Office 365 applications) per user’s FSLogix Profile Container, with ~10x during sign in and sign out is adequate to use as a rule of thumb – preferred below the 5 ms (the lower the better).
- Getting started with FSLogix profile containers on Azure Files in Azure Virtual Desktop
- Create an FSLogix profile container for a host pool using Azure NetApp files
Download the FSLogix agent and install it in your Azure Virtual Desktop image – virtual machine. FSLogix is available for download here
Install the FSLogixAppsSetup agent in the image
Wait for the installation to be finished…
The configuration part of FSLogix Profile Container can be performed in either registry settings or group policy files. The most simple and effective method is using the registry settings below.
Open regedit.exe and browse to “HKEY_LOCAL_MACHINE\Software\FSLogix\Profiles”
Create a REG_SZ value name “VHDLocations” and enter new Azure Files network file share path (e.g. \\fslogixwvddemo.file.core.windows.net\fslogixprofiles)
Create a DWORD value name “Enabled” and give it value 1.
Create a DWORD value name “DeleteLocalProfileWhenVHDShouldApply” and give it value 1. The one deletes existing local profiles before logon – this avoids errors.
Create a DWORD value name “FlipFlopProfileDirectoryName” and give it value 1. The one changes the folder name to USERNAME-SID which is much easier during troubleshooting or maintenance search-related work.
Tip: The most important settings for the usage of FSLogix Profile Container are the Enabled and VHDLocations registry setting. There are some other settings that I default recommend to enable. The VolumeTypesetting changes to disk type to VHDX. You can provide more maintenance tasks via PowerShell with VHDx so I advise changing that from default VHD to VHDx.
Note: If you are using Windows 10 Enterprise single and multi-session or Windows Server 2019, you don’t have to enable the RoamSearch setting. The Search DB is already stored in your user profile.
See here all the other advanced registry settings for FSLogix Profile Container. The example below is with Azure Files.
Looking for more best practices, please visit our new Azure Solutions Center page on – FSLogix for Enterprises here.
Make sure to configure the following Antivirus exclusions for FSLogix Profile Container.
- Exclude Files:
- %ProgramFiles%\FSLogix\Apps\frxdrv.sys
- %ProgramFiles%\FSLogix\Apps\frxdrvvt.sys
- %ProgramFiles%\FSLogix\Apps\frxccd.sys
- %TEMP%\*.VHD
- %TEMP%\*.VHDX
- %Windir%\TEMP\*.VHD
- %Windir%\TEMP\*.VHDX
- \\server\share\*\*.VHD
- \\server\share\*\*.VHDX
- Exclude Processes
- %ProgramFiles%\FSLogix\Apps\frxccd.exe
- %ProgramFiles%\FSLogix\Apps\frxccds.exe
- %ProgramFiles%\FSLogix\Apps\frxsvc.exe
Enable the Screen Capture Protection feature
To enable the Screen Capture Protection feature, which I’m explaining here – you only have to run the command below to add the designated registry key to enable the feature – in your image. More info can be found here on Microsoft Docs.
Note: The feature currently only works for full desktop sessions from Windows 10 endpoints, Windows Desktop client, version 1.2.1526 or later is needed and your session hosts – host pool should be active in the validation environment.
reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services" /v fEnableScreenCaptureProtection /t REG_DWORD /d 1
Additional image optimizations
Run the following PowerShell commands to optimize the images based on the recommendations here.
Disable auto-updates
reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU" /v NoAutoUpdate /t REG_DWORD /d 1 /f
Time zone redirection
reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services" /v fEnableTimeZoneRedirection /t REG_DWORD /d 1 /f
Disable Storage Sense
reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\StorageSense\Parameters\StoragePolicy" /v 01 /t REG_DWORD /d 0 /f
Finalize (sysprep) the Windows 10 multi-session image
Sysprep (Generalize) your image and shut down the virtual machine.
Note: You can also perform this action directly from the Azure portal – during the Managed image capturing process.

To wrap the Windows 10 Enterprise multi-session image up and start the host pool enrolment process from the Azure Marketplace, we must shut down the virtual machine to release the image.
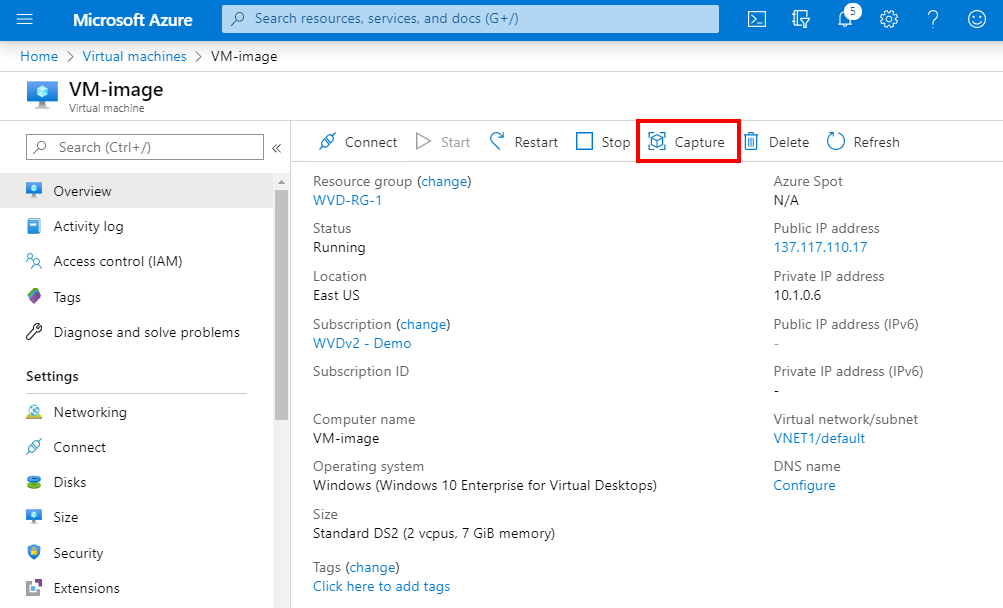
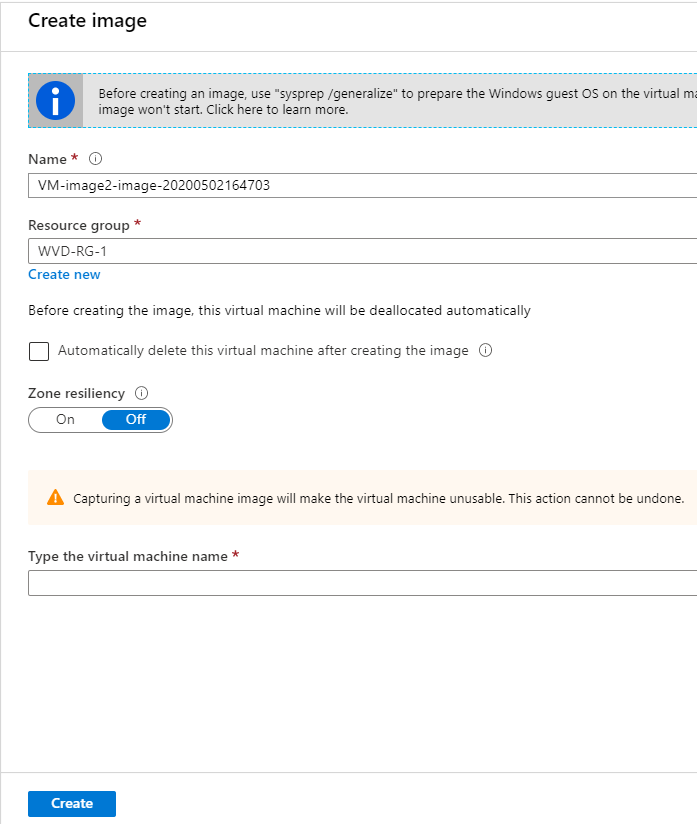
Capture the custom – Azure Managed – image
Create an Azure managed (custom) image from the VM in the Azure portal. Click on Capture
Note: The benefits of using an Azure Managed Image is that everything that you install will be used as the baseline for the enrolment later during the Azure Marketplace procedure. All the virtual machines you select to enrol will include all the same software as you now install. For 500 virtual machines that save a lot of post-installation work. Of course, you can use your own automation solution and build images from scratch and add your software afterward (post-installation) – it’s all up to you!
Create the image. Enter the Name and Resource group. You can provide your own versioning in the name.
Note: If the enrolment fails based om the Managed Image your created, it could be that the VM on Azure didn’t pick up the Generalized status on the VM level. You can force this by running the PowerShell command below.
Set-AzVm -ResourceGroupName $rgName -Name $vmName -Generalized
Update 20.11.2020. You can now directly export the captured image as well into the Azure Shared Image Gallery (SIG), as part of the recent improvements of the service. You can read more about it here, it looks amazing and removes a lot of pre-steps in this article to create the shared image gallery separately.
Optimize your images with the Virtual Desktop Optimization tool
The virtual desktop optimization tool makes it possible to disable uncommon services for virtual desktop environments, such as Azure Virtual Desktop. Read this article to learn more about the (Windows) Virtual Desktop Optimization tool.
Note: We recommend running the script below after the sysprep process. Most likely as a startup script while you have to deal with a large set of virtual machines.
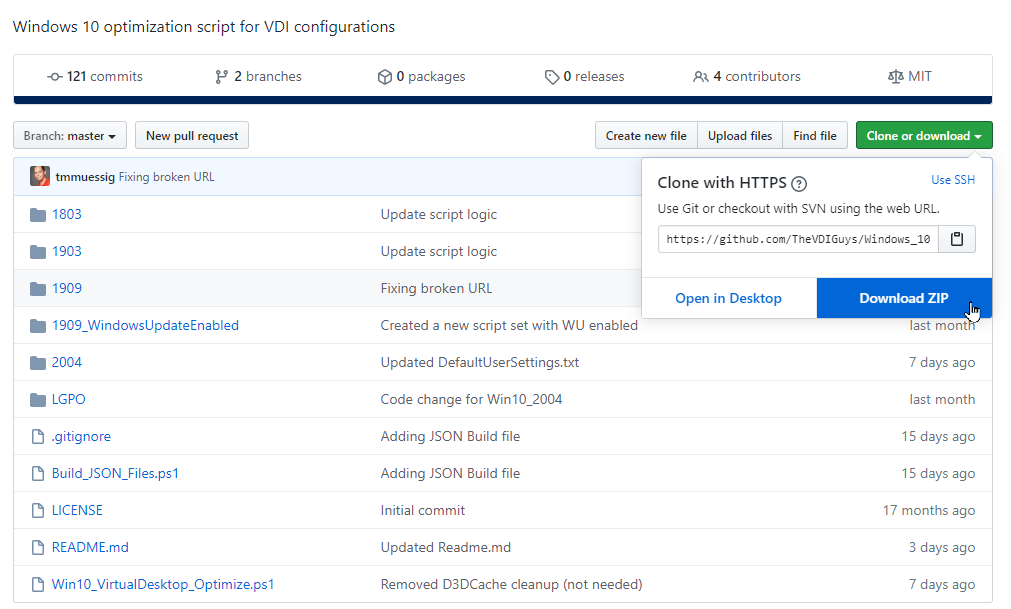
Download all the scripts from the public Github repository below
Click on Clone or Download followed by Download ZIP.
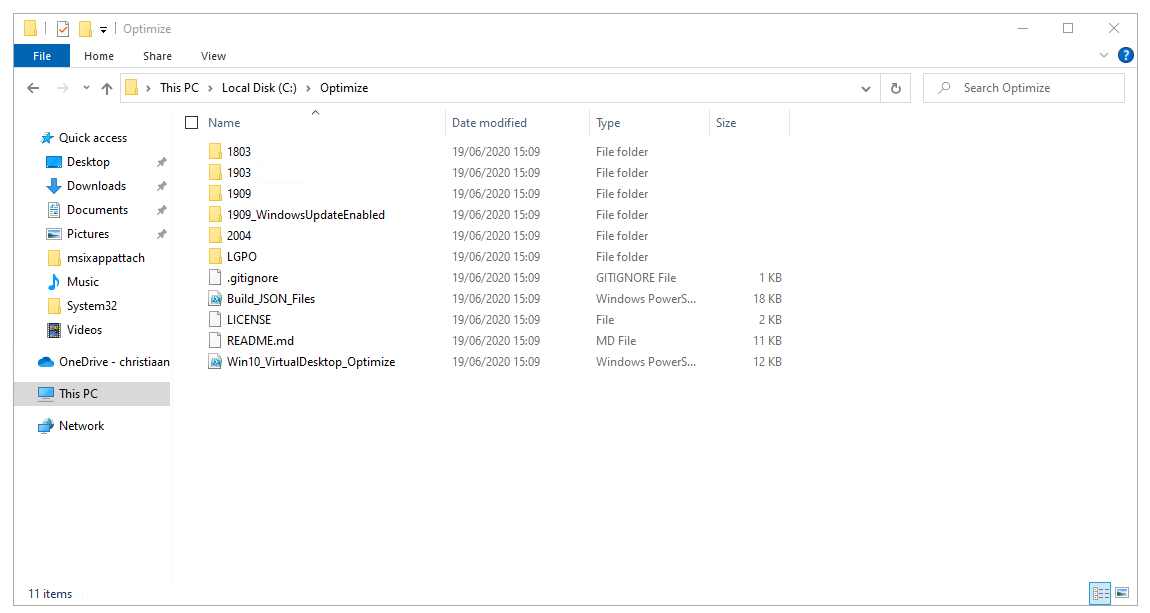
Unzip the folder to your Azure Virtual Desktop – session host(s) – in a random folder (ex. C:\Optimize or C:\Temp).
Note: You could also run the scripts as part of your image management procedure e.g. Azure image Builder (AIB) or Azure DevOps if you like.
Important information before you start running the tool
There are settings default disabled when you run the scrip out of the box such as AppX Packages for the Windows Calculator. We strongly suggest analyzing the tool via the JSON files that include the default settings. This also gives you the opportunity to enable them before running the tool so they remain untouched.
You can find the JSON file in the Windows built number folder, under ConfigurationFiles – e.g. C:\Optimize\2004\ConfigurationFiles.
You’ve to put the settings to Enabled – that you want to keep as default. Below is the example file for AppX Packages, there are JSON files for Services and scheduled tasks as well.
Another option is to remove the whole entry out of the JSON file.
AppxPackages.JSON – Example Windows Calculator App
{
“AppxPackage”: “Microsoft.WindowsCalculator”,
“VDIState”: “Enabled“,
“URL”: “https://www.microsoft.com/e…“,
“Description”: “Microsoft Calculator app”
},
Services.JSON – example Windows Update Service
{
“Name”: “UsoSvc”,
“VDIState”: “Enabled“,
“Description”: “Update Orchestrator service, manages Windows Updates. If stopped, your devices will not be able to download and install the latest updates.”
},
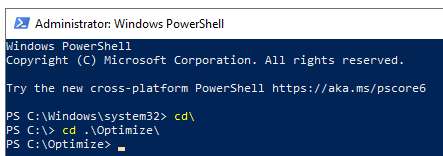
Start PowerShell – Run as Administrator
In PowerShell, change directory to the scripts folder (e.g. C:\Optimize or your own specific folder)
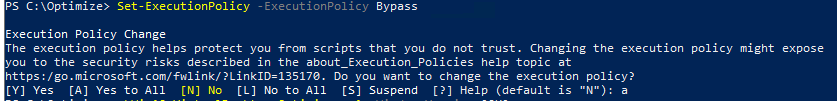
Run the following command to make running possible
Set-ExecutionPolicy -ExecutionPolicy Bypass
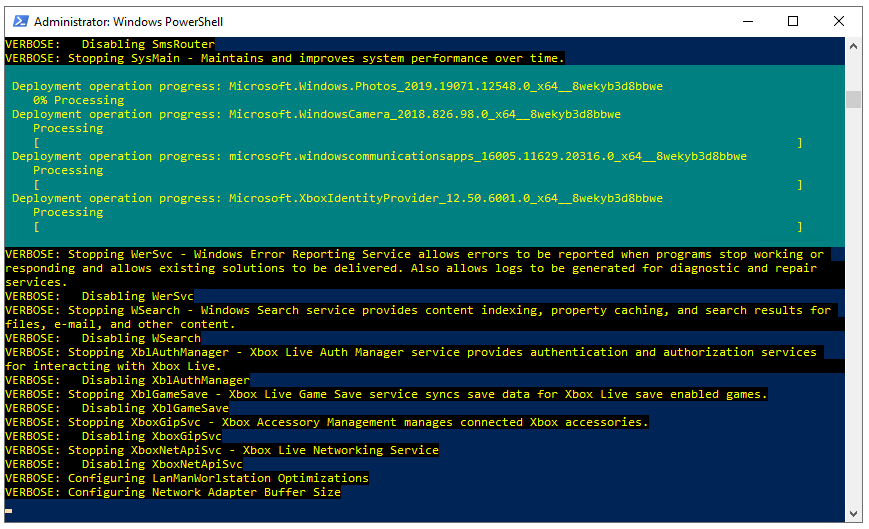
Run the VirtualDesktopOptimizationTool steps – by running the command below.
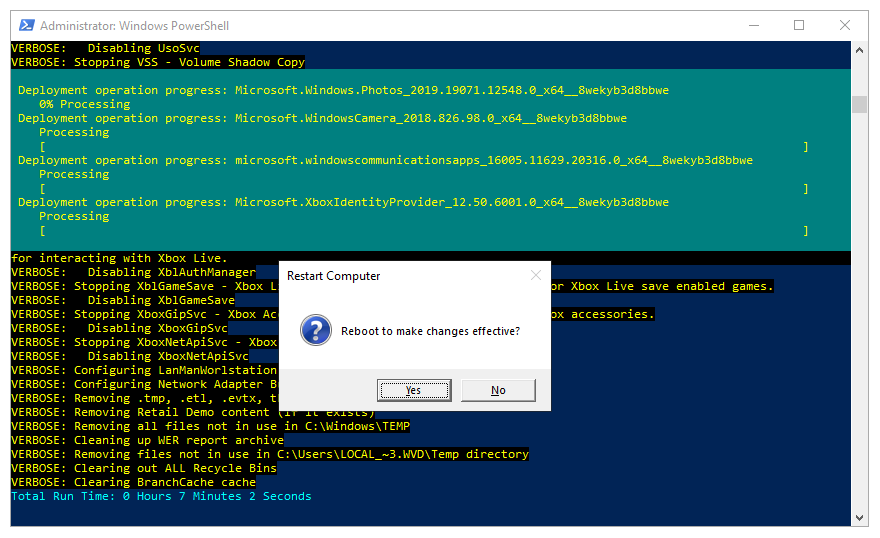
.\Win10_VirtualDesktop_Optimize.ps1 -WindowsVersion 2004 -Verbose
Note: When you use a different build of Windows 10, you must change the WindowsVersion parameter. Build 1803 and up are supported as well for Windows 10 Enterprise. Windows 10 multi-session support applies only to build 2004.
When complete, you should see a prompt to restart.
Reboot the session hosts(s)
Do you have any feedback – or questions about the optimization tool above? Please use our Tech Community platform here to ask questions.
We recently had the creators of the Virtual Desktop Optimization tool as guests on our Desktops in the Cloud video-podcast. Robert and Tim explained everything you should know, as well as best practices and lessons learned. A must watch in extension to this article. Watch it below.
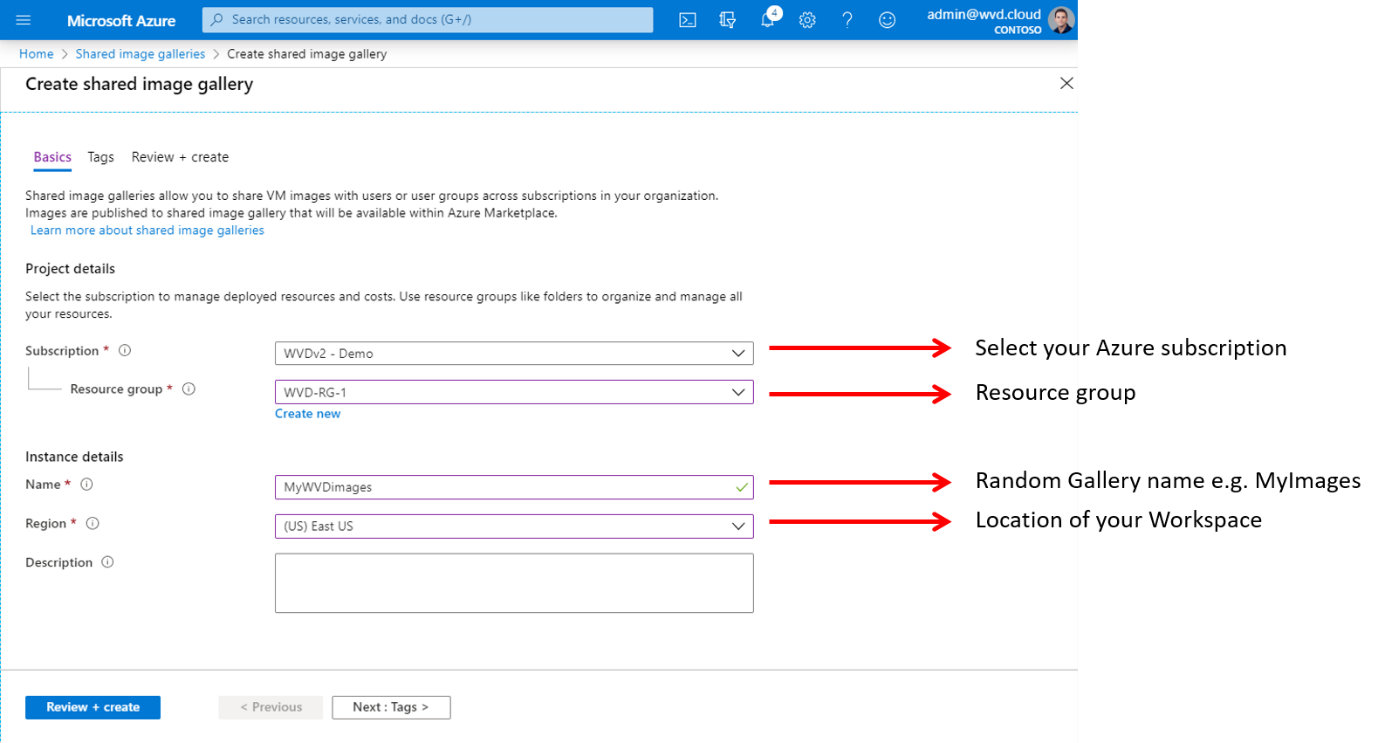
Create an Azure Shared Image Gallery (SIG)
Note: The step below is optional. You could deploy a host pool based on an Azure managed image (only) as well.
You also have the option to use the Azure Shared Image Gallery (SIG) within Azure Virtual Desktop as a source for your images. You can share your images to different users, service principals, or AD groups within your organization. Shared images can be replicated to multiple regions, for quicker scaling of your deployments. Read more about it here.
- Managed global replication of images.
- Versioning and grouping of images for easier management.
- Highly available images with Zone Redundant Storage (ZRS) accounts in regions that support Availability Zones. ZRS offers better resilience against zonal failures.
- Sharing across subscriptions, and even between Active Directory (AD) tenants, using RBAC.
- Scaling your deployments with image replicas in each region.
Additional tips and tricks. If you are not aware of Azure Image Builder, please have a look here. I also recommend to watch this Ignite session. The process works pretty simple and could simplify how you do update and image management today as you can easily create new images based out our Azure Marketplace gallery which receives all the latest updates directly after patch Tuesday. In this (below steps) article we use the manual approach via the Azure Managed image creation process.
More info on automation scripts for FSLogix and templates for AIB can be found here: https://aka.ms/azvmimagebuildertesting.
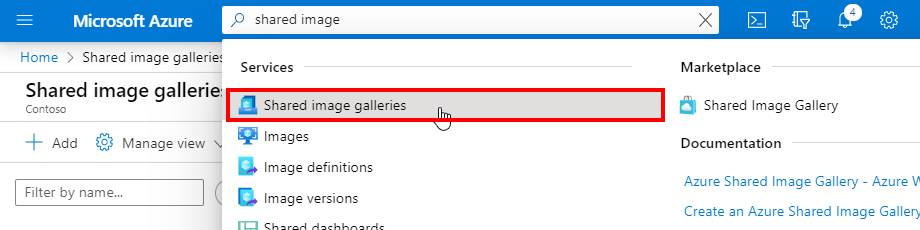
Let’s start the creation of the shared image out of a Azure Managed Image
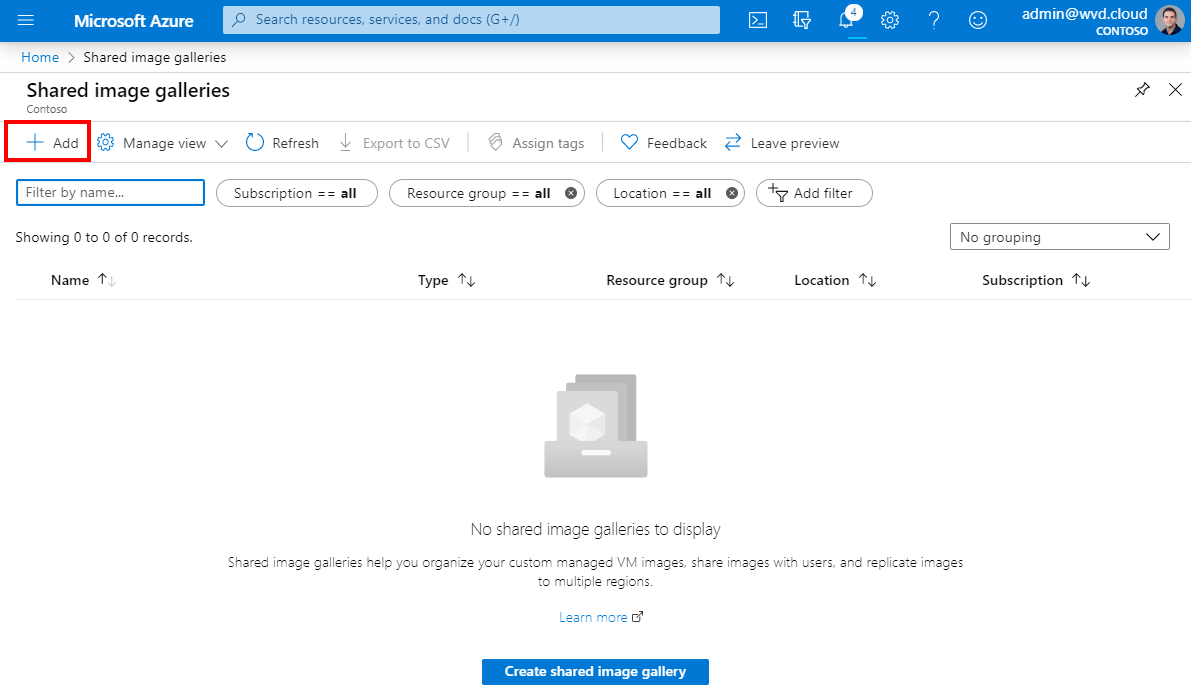
Look for Shared image galleries in the Azure menu
Click on Add
Create the Gallery
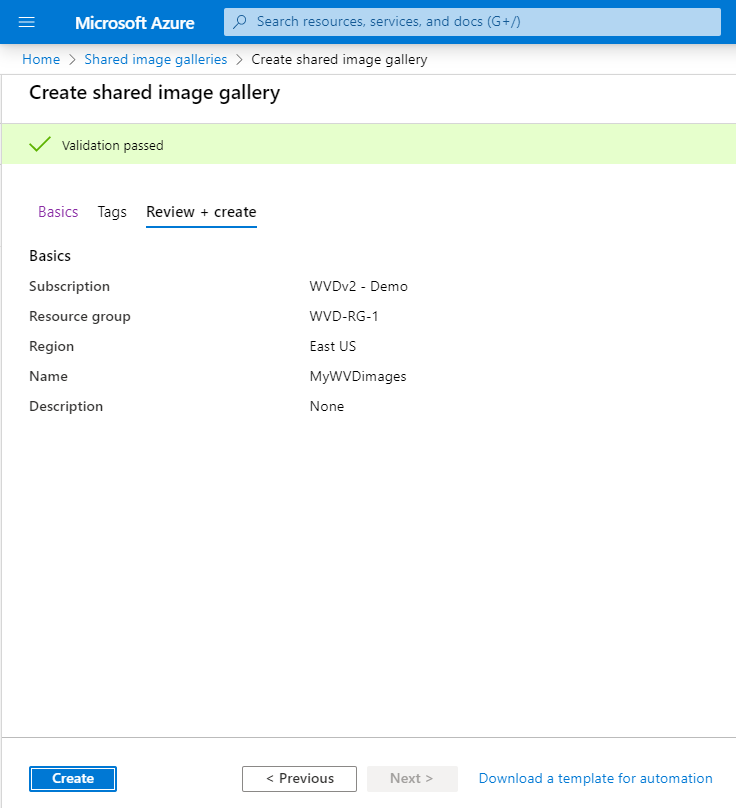
Click on Review + create
Click on Create
Open the new created Gallery
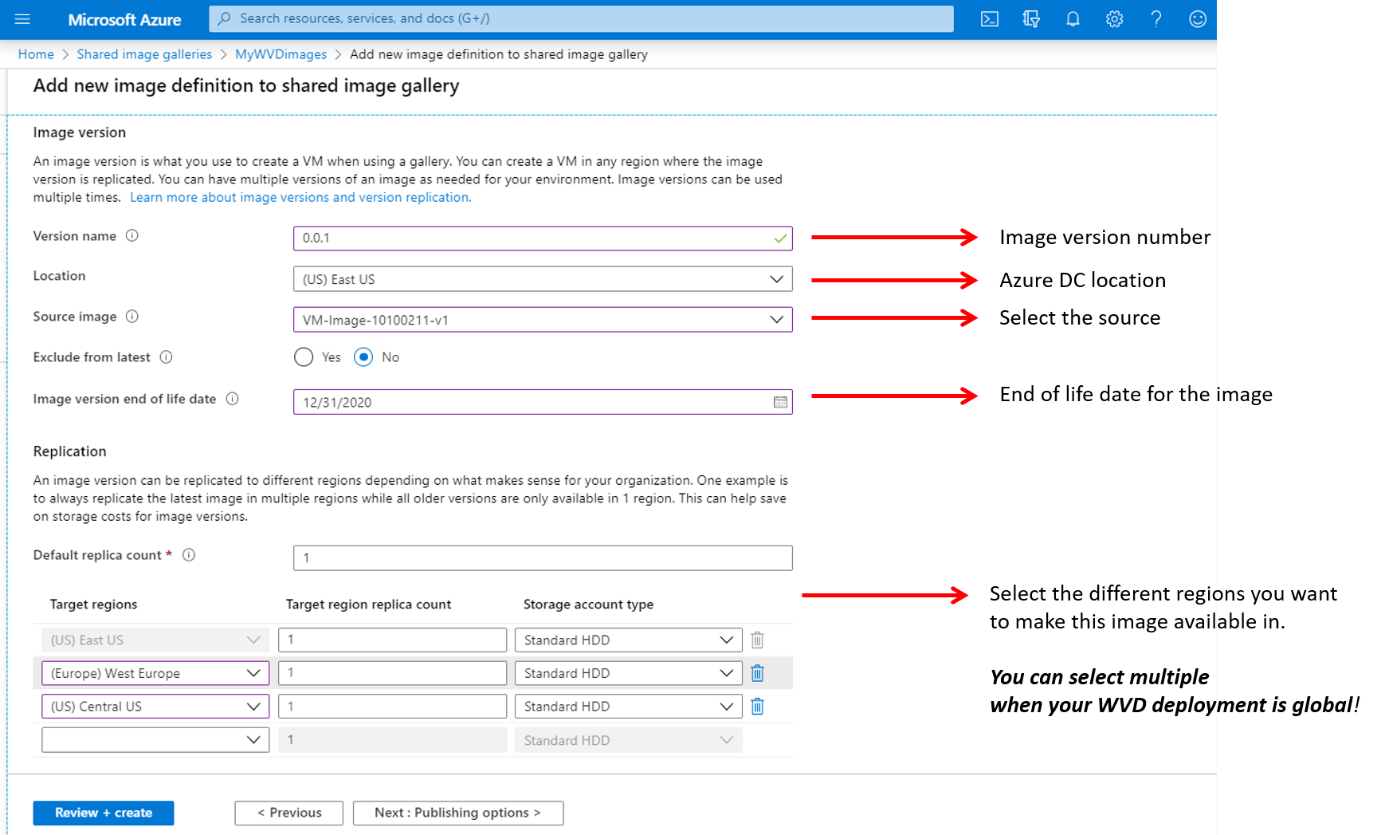
Click on + Add new image definition
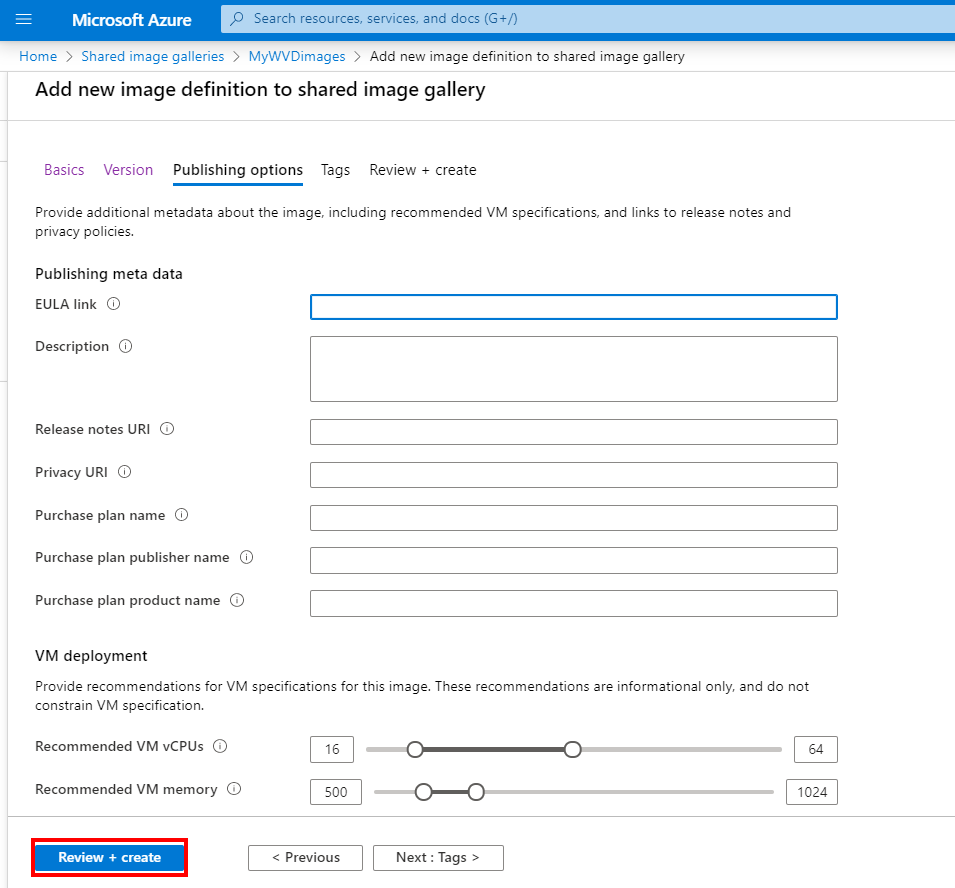
Fill in the required information as similar below
Click on Next: Version
Note: EMS stands for (Windows 10) Enterprise multi-session.
Give in a major/minor patch number for doing proper versioning. Take over the settings as below based on your pre-created Azure Managed image.
Select the different regions you want to make this image available in. You can select multiple when your AVD deployment is global! Pretty cool though.😊
Click on Next: Publishing options
Note: The image version name should follow Major(int).Minor(int).Patch(int) format. For example: 0.0.1, 1.5.13. Also, make sure the setting “Exclude from latest” stays on No.
The following settings are optional and just recommendation that we not going to use as we define the size via the host pool enrolment process of Azure Virtual Desktop.
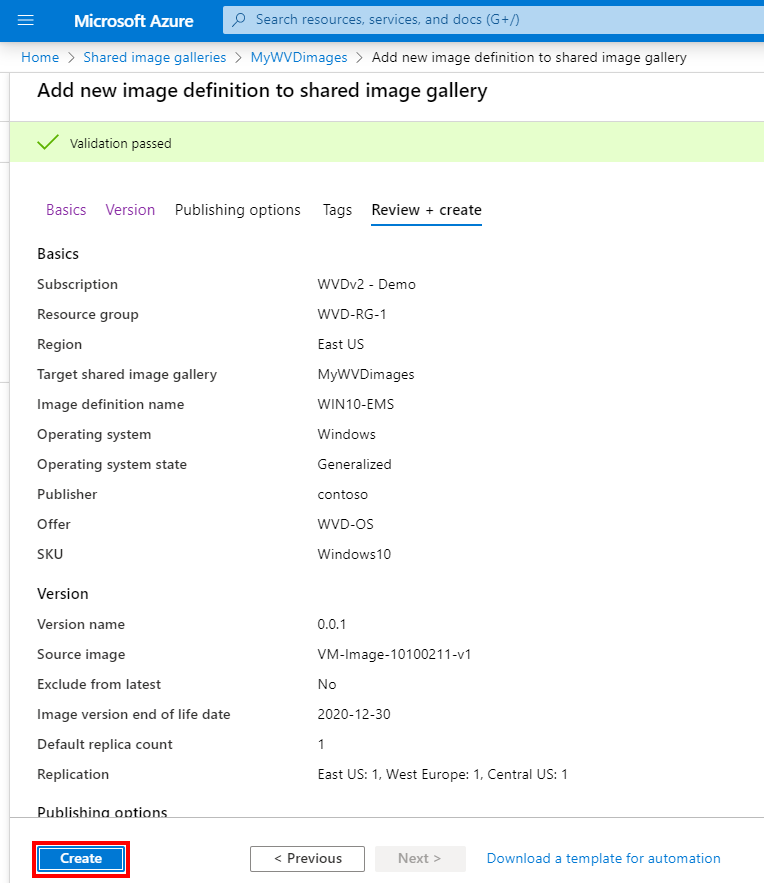
Click on Review + create
Click on Create
Your Shared Gallery image(s) (SIG) will now be created and distributed across the different regions and ready to use as source for the next steps!
Perform the Microsoft.DesktopVirtualization resource provider registration
Open the Azure Subscriptions services menu
Open the Azure subscription where you are going to deploy your Azure Virtual Desktop environment
Click on Resource providers
Search for the Microsoft.DesktopVirtualization – provider and click Register
Confirm the registration. There must be a green checkbox next to the Microsoft.DesktopVirtualization provider as in the screenshot below.
Now we are done with the pre-steps. We can now start with the enrolment process.
Create your host pool
Now we come to the point where we can use our master image as baseline of our deployment. A host pool is a collection of session hosts (right now based on Windows 10 – Multi User, however Windows 7 and Server 2012 R2 and higher is supported as well). We can use them later to assign our Desktops and Published Apps to.
Search for Azure Virtual Desktop in the Azure menu
Note: The new ARM templates for Azure Virtual Desktop ARM-based to automate your deployment are now available for download here.
Create a host pool
Click on Create a host pool
Choose your subscription, metadata location and host pool properties
Click on Next: Virtual Machines
02.17.2021: Metadata locations are now also active in North and West Europe as a selection option. This location cannot be changed afterward.
Using Windows 10 single session? Make sure to change the host pool type to personal.
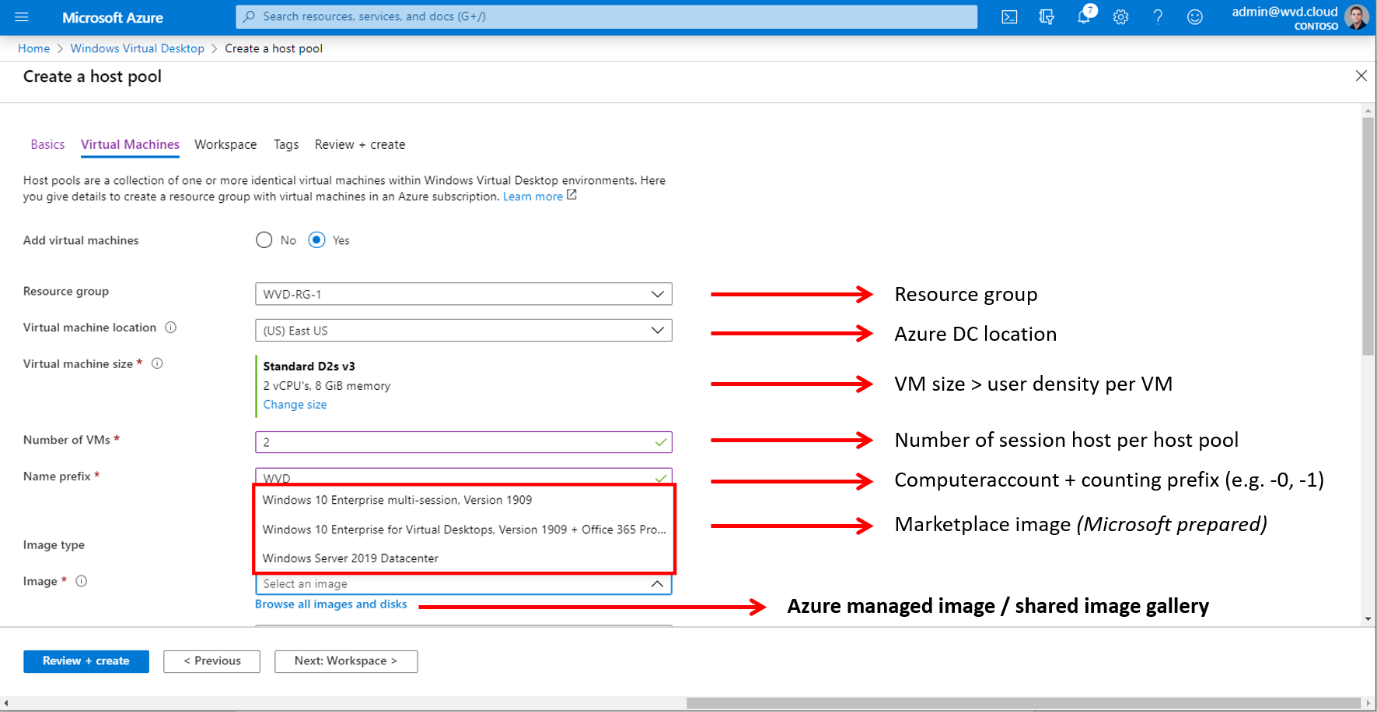
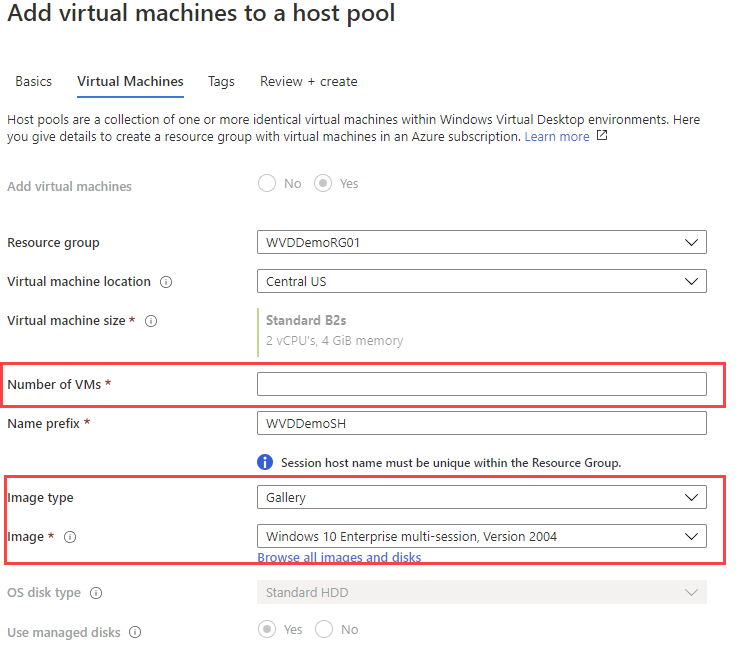
VM details
First click on Yes
Give in the VM details –select the size and image for your enrolment.
Note: Office 365 ProPlus has been renamed to Microsoft 365 Apps for Enterprise.
Note: You can deploy in West Europe, this Azure datacenter location is where you deploy your virtual desktop – session hosts in. This is independent of the metadata location.
Note: Session hostnames cannot exceed 10 characters due to the auto-count prefix that comes extra.
Note: The following three articles lists the maximum suggested number of users per virtual central processing unit (vCPU) and the minimum VM configuration for each workload. This could be helpful to see what your first estimation of VMs as part of your host pool.
- Multi-session recommendations
- Single-session recommendations
- General virtual machine recommendations
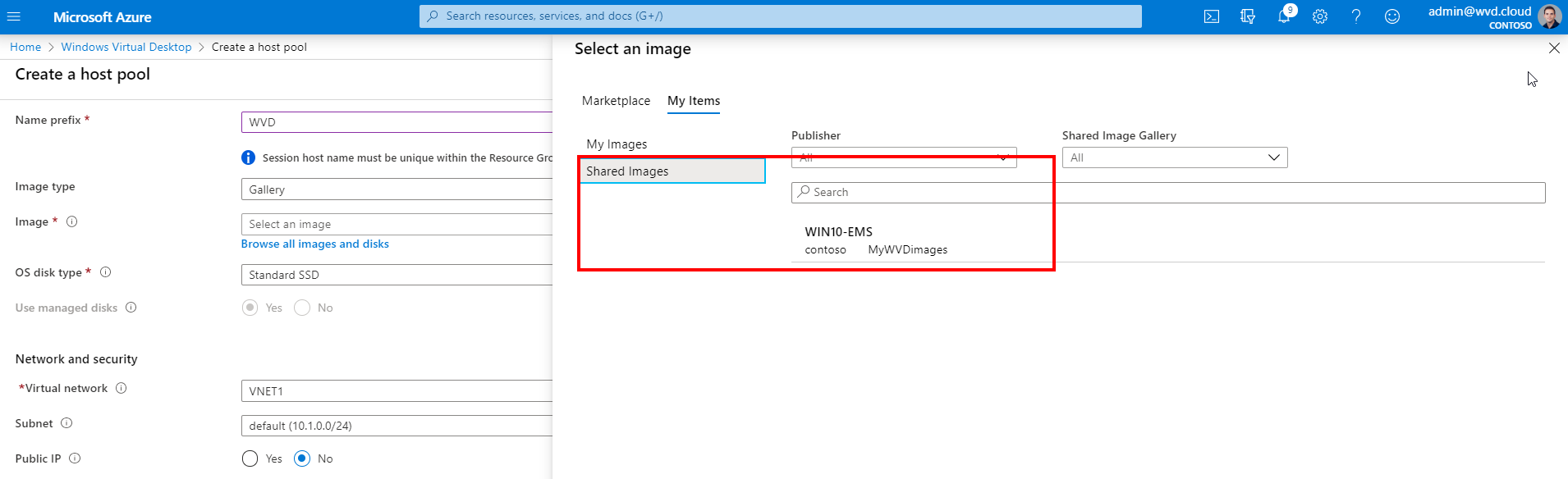
Select your image type
Skip this step here if you are not using a custom image, and decided to go for one of the Marketplace images (Microsoft prepared). You must install apps, and agents such as FSLogix and OneDrive afterward.
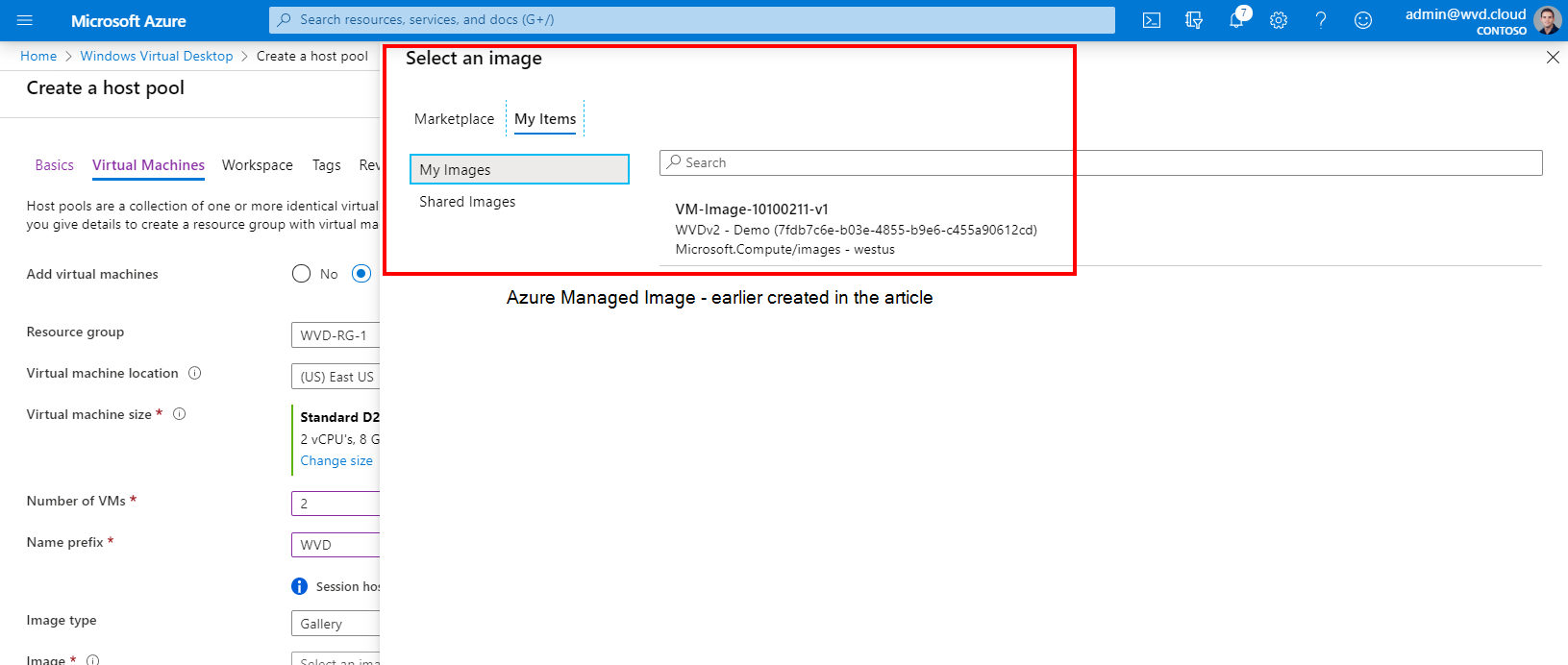
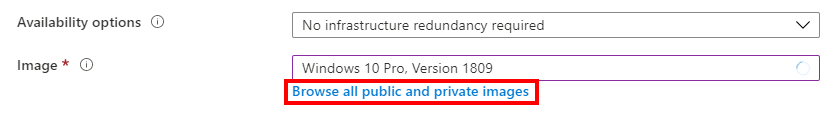
Click on Browse all Images
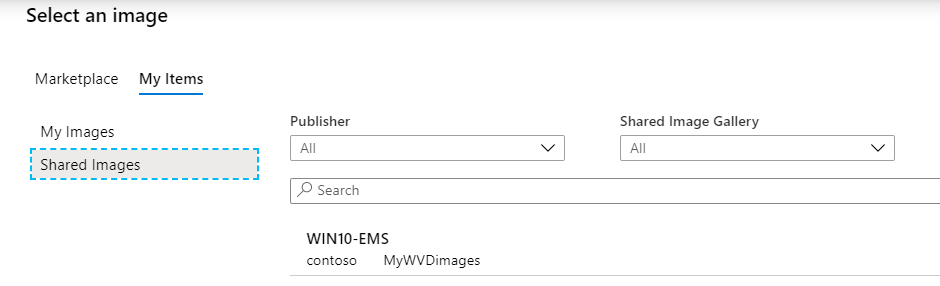
1: My image. You can now also instantly update host pools that are created based on Azure Managed images (images under My images) as part of the host pool.
Note: It’s now possible to change this option after the creation of the host pool, also Azure Managed images!
2: Shared images(SIG). The Azure shared image gallery (SIG) comes in very handy due to the support for versioning as well as global image replication accross regions, read the benefits again here. It will automatically pick and select the latest image version.
Once you need to update your existing host pool, you only have to deploy new session host VMs and drain old VMs and your host pool is up to date again! I’ll explain how you update the image later on here.
Select our custom created Windows 10 Enterprise multi session Azure Managed image / or the one from the shared image gallery (SIG)
Note: New feature. It’s now possible to change this option after the creation of the host pool (while clicking on “Add virtual machines to a host pool), also Azure Managed images!
Network and security
Provide the properties for your Azure Virtual Network to join your session hosts in.
Note: Make sure that the DNS servers of your Azure VNET are pointing to the domain controllers DNS servers to make sure the FQDN can be resolved!
Note: Also make sure that all the URLs below are reachable from that VNET!
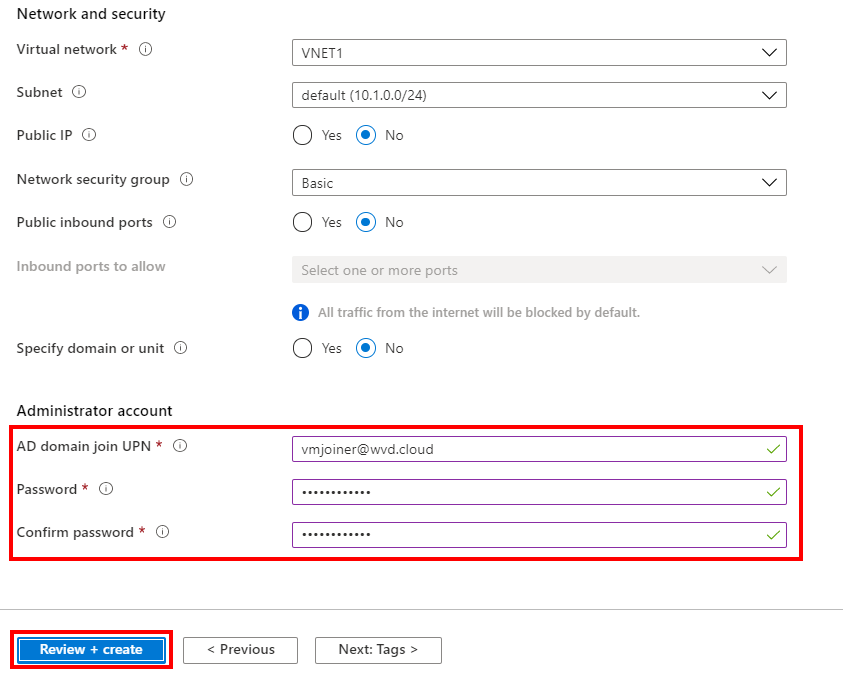
Administrator account
Enter in a service account to join your session hosts to your AD (Kerberos – ADDS) domain
Click on Next: Workspace
Create the Workspace
The Workspace is the new name for tenant. We can now create this directly do this in the Azure Portal instead of using PowerShell before!
Click on Yes and Create new
Give in a name for your Workspace (tenant)
Click on Ok
Click on Review + Create
Start the enrolment
Review your settings – click on Create to start the deployment
Create and Assign Remote Applications (to AAD Groups!)
The process of publishing applications has become easier as well. First you must create a application group based on Remote app as type.
Select your host pool and resource group properties
Select either a user or Azure AD group to make it more Dynamic. Yes we support Azure AD groups!
Add your (Remote) application from the start menu from the session host to publish
Select your Workspace
You can also easily adjust existing host pools (RemoteApp) and add new Applications on the fly!
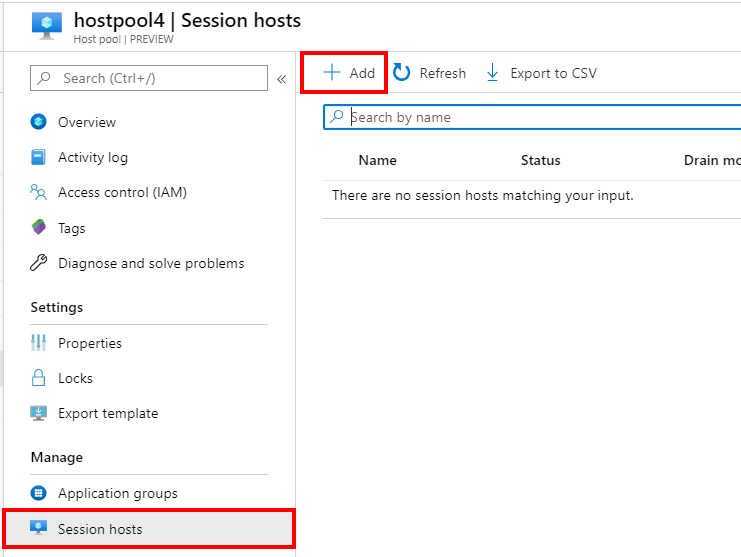
Add session hosts to existing host pool
Great enhancement. Since the new ARM based Portal release – you are able to expand host pools easily based on existing images.
Note: The designated ARM templates that can do this will follow later.
Click on + add in the host pool
Follow the requirements and add extra machines to the host pool!
Note: This procedure works for as well Azure managed images and shared images. You can now change the source of the Image as well. This is great news for image updates.
Update the host pool images – create a new image version
The maintenance process of your Azure Virtual Desktop environment is just as important as the enrolment process. The prior created Azure Managed Image – we used as custom image can be used again to use as baseline to provide the extra updates on top. .
First you need to apply your updates to your image. This obviously could be anything, such as LOB application updates, agents or just the FSLogix client as example.
You can create a new Virtual Machine from the Virtual Machines (IaaS) menu (not the host pool this comes later) with the previous version (or another version if you want to revert more changes) – and spin that machine up.
Select the source version – it will automatically pick the latest version.
After the VM enrolment is done, install all the updates on the VM. This can be done automated or manually (use RDP or Azure Bastion to secure remote into the VM – image)
Now we need to sysprep (generalize) the machine and make sure to capture it again as image.
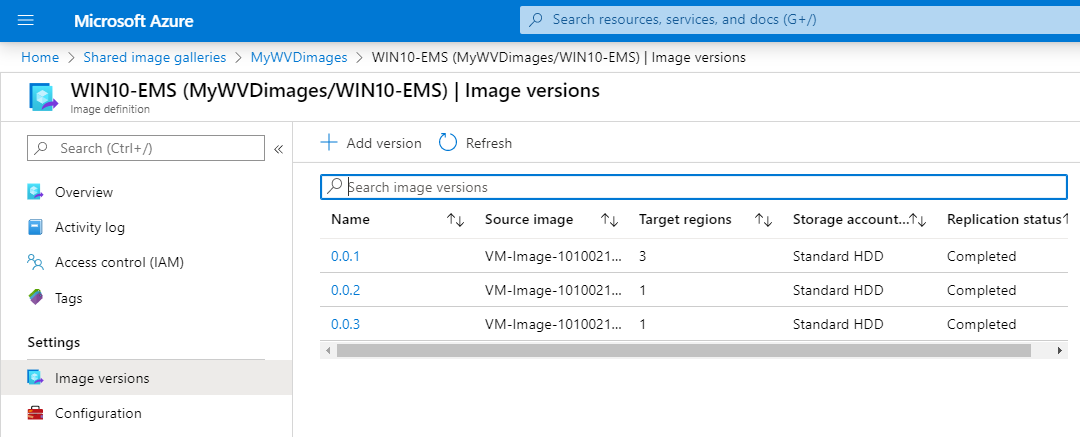
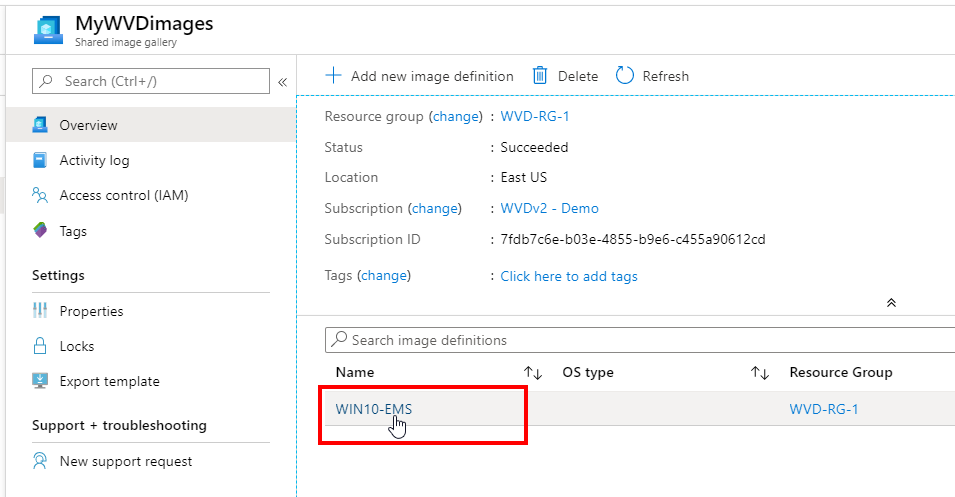
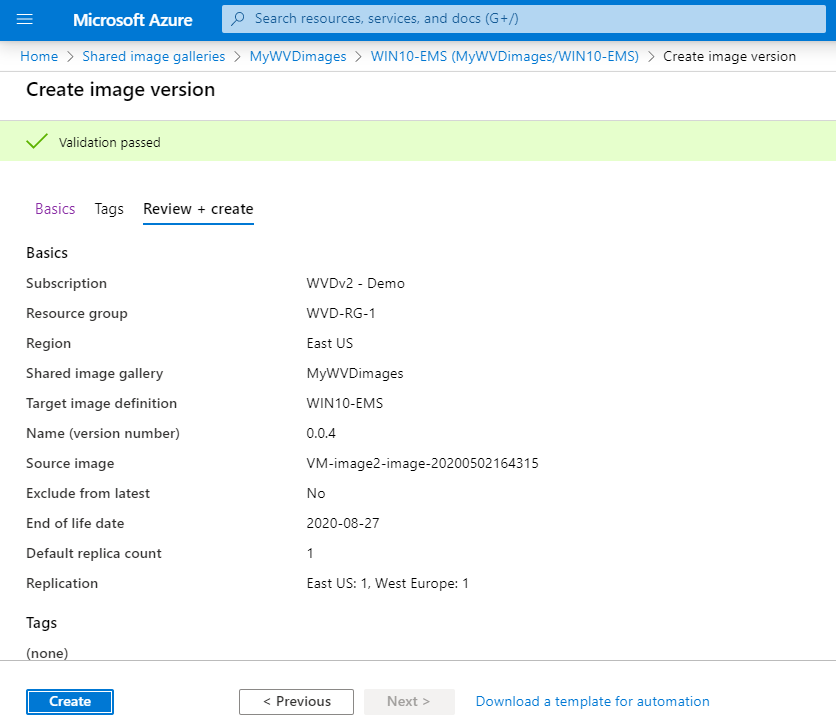
Go back to your Shared image gallery
Open your existing shared image, for me that’ll be WIN10-EMS
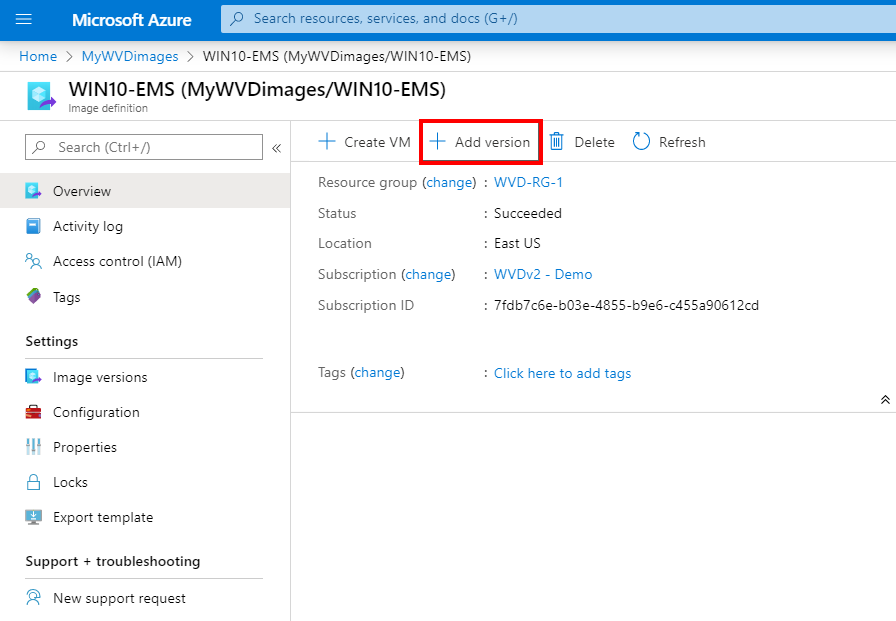
click on + add version
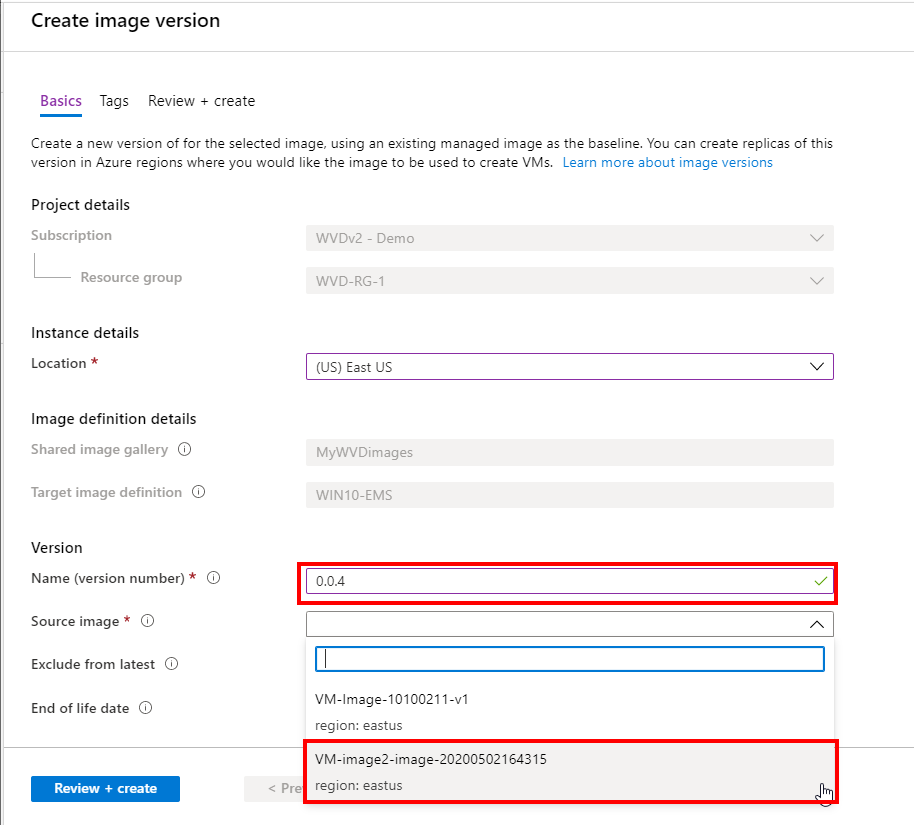
This is the most important part. Make sure to select the new Azure Managed image (from the last capture process) as source with (of course) a new versioning number to make sure the host pool enrolment picks the latest newest version as default.
Select the End of life date and DC locations (if any) to make this new image available in as well.
Click on Review + create
Note: Make sure that the option, Exclude from latest is set to NO. If this setting isn’t configured in the right manner – the host pool process will not pick the latest version as source!
Click on Create
We can start with adding sessions hosts to the designated host pool.
Go to your host pool that was previously configures with shared images (SIG) as source.
Click on + Add
Note: We are adding extra machines to the host pool. Make sure to put the older versions in drain mode, or remove them to make sure new user sessions are logging on to the new image version.
Click on Virtual Machines
Enter in the Number of VMs to add/update to the host pool (based on the new image – that’s why the numbering and latest setting is so important while creating the host pool).
Note: As said earlier. It’s now possible to change the source of the image – this is a great improvement that leaves you in the position to change more easier to Azure Managed Images versions – or potentially swaps between SIG.
Select your Azure Virtual Network (VNET) and AD join service account credentials.
Click on Review + create
Click on Create
Post-enrolment host pool automation (optional)
Note: You can also add machines manually to the host pool by installing the AVD Agent and bootloader on your virtual machine – during the installation it will ask for a token. You can request (or create a new one) via this PoSH command Export-AzAVDRegistrationInfo to create a new registration token – or Get-AzWvdRegistrationInfo to export an existing token. Download the Azure Virtual Desktop Agent and bootloader the Azure Virtual Desktop Agent Bootloader here. You can use the silent (automated) commands below to install the AVD agents without manual interaction in each VM! One for the AVD agent and the other one for the AVD bootloader agent.
AVD Agent command
Start-Process -FilePath "msiexec.exe" -ArgumentList "/i $AgentInstaller", "/quiet", "/qn", "/norestart", "/passive", "REGISTRATIONTOKEN=$RegistrationToken", "/l* C:\Users\AgentInstall.txt" -Wait -Passthru
Bootloader command
Start-Process -FilePath "msiexec.exe" -ArgumentList "/i $AgentBootServiceInstaller", "/quiet", "/qn", "/norestart", "/passive", "/l* C:\Users\AgentBootLoaderInstall.txt" -Wait -Passthru
Change the name of your Workspace
It could be helpful and more customer friendly to change the name of the Azure Virtual Desktop environment to Azure Virtual Desktop like in the example below, or your customer name. I’ll explain how you can do that.
Go to your Workspace properties in the Azure Portal and change the Friendly Name
Change the name of your Virtual Desktops
The same for your Virtual Desktop names. There’s also an option to change them something custom such as Session Desktop as example below.
Go to the Application Group and open the properties
Change the friendly name to anyone you like
Install the Azure Virtual Desktop Client
To run your Azure Virtual Desktop – Full Desktops or RemoteApps directly from the client and/or start menu, you must install the AVD Client.
Download the AVD client below
http://aka.ms/wvd/clients/windows
Start the AVD Client – Desktop app
Click subscribe with URL
Enter the following ARM-based – https://rdweb.wvd.microsoft.com/api/arm/feeddiscovery – URL.
Do you prefer to enter your organization’s email?
Please make sure to create the following TXT DNS record in your verified domain that you use within Azure AD as primary domain. After that, you will be able to instruct your users to enter in the email address only.
DNS Settings
| Name | Type | TTL | TTL |
| _msradc | TXT | 1 | Hours |
| Value |
| https://rdweb.wvd.microsoft.com/api/arm/feeddiscovery |
Continue with the client configuration steps.
Enter a user that has a desktop or apps applied.
Click on Next
Enter your credentials
Provide Azure MFA (if activated).
Note: When you use Azure MFA you might want to take a look at one of my other articles here as well to enforce or whitelist Azure MFA for your end-users for the Windows Client.
Your RemoteApps and Desktops are ready to use!
Deploy the Remote Desktop Client via Microsoft Endpoint Manager – Intune
I’ve recently written an article on how to deploy the Remote Desktop (MSRDC) AVD client as Intune Win32 app – via Microsoft Endpoint Manager (MEM) to your physical clients. You’ll learn in this article how you can publish the Azure Virtual Desktop Client Application (MSRDC) to your endpoints via Microsoft Endpoint Manager (Intune).
Use the HTML5 Web portal
AVD can be accessed without a client or agent from a web browser, which can be beneficial when you need to do some work without having your own device with you.
To access the RDWeb portal, please go to the short link https://aka.ms/wvdarmweb or https://rdweb.wvd.microsoft.com/arm/webclient in full length.
Logon with your credentials.
Azure MFA can be added to this as well. Azure AD Conditional Access features are supported!
If you get access, you’ll see all your Desktops and RemoteApps
 We are inside our Windows 10 multi-session – session host, including OneDrive, Teams and Outlook – everything just works 😊!
We are inside our Windows 10 multi-session – session host, including OneDrive, Teams and Outlook – everything just works 😊!

Some extra information regarding client supports; Azure Virtual Desktop supports the following clients as of today.
This URL goes directly to the official Microsoft download page to download the AVD client.
- Windows 10
- Windows 7
- Android
- Chromebook*
- Samsung DeX
- HTML5 Web client on Windows, macOS and Linux
- Linux SDK – zero /thinclients (via IGEL Next-gen OS)
- Which basically means every device is supported with a HTML5 browser installed.
Keep in mind to open up the URLs and ports below from your client network environment to make AVD work. You can find the full list here.
See here a comprehensive troubleshooting overview and what to do when for feedback and support!
https://docs.microsoft.com/en-us/azure/virtual-desktop/troubleshoot-set-up-overview
Hope to see you back soon – and feel free to leave a comment if you’ve any questions.
Want to see everything above in action?
I recently was a guest at the famous Azure Friday (channel 9) show with Scott Hanselman. I talk about almost everything that you learn in this article however in all live demos. Watch it back below.